
CVE-2017-14798 Exploit Step-by-Step
CVE-2017-14798 is a Common Vulnerabilities and Exposures (CVE) identifier for a race condition vulnerability in the PostgreSQL init script. This vulnerability allows an attacker with access to the PostgreSQL account to escalate their privileges to root.
The vulnerability was discovered by security researcher Kamil Khadeyev and reported to the PostgreSQL project in May 2017. A patch was released in June 2017.
The vulnerability was exploited by attackers to gain root access to a number of PostgreSQL servers. This allowed the attackers to steal data, install malware, or disrupt service.
Severity: Critical
CVSS Score: 9.8
Description: A race condition vulnerability in the PostgreSQL init script allows an attacker with access to the PostgreSQL account to escalate their privileges to root.
Impact: This vulnerability allows attackers to gain root access to a PostgreSQL server, which could allow them to steal data, install malware, or disrupt service.
Mitigation: Users should upgrade to a patched version of PostgreSQL and ensure that their PostgreSQL accounts are properly configured with strong passwords and other security measures.
Step-by-Step Guide:
1. Exploit Information:

Exploit Title: The title or name of the exploit.
Date: The date when the exploit was discovered or released.
Exploit Author: The person or organization who discovered or authored the exploit.
Vendor Homepage: The website of the software vendor where the vulnerability was reported.
Software Link: The link to the software affected by the vulnerability.
Version: The specific version of the software that is vulnerable.
Tested on: The specific operating system or environment where the exploit was tested.
CVE: The Common Vulnerabilities and Exposures (CVE) identifier assigned to the vulnerability.
2. Script Execution
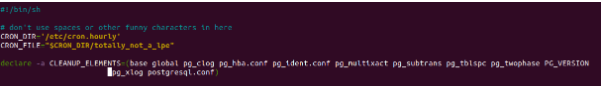
Shebang: The shebang line specifies the interpreter to be used, in this case, /bin/sh (the Bourne shell).
CRON_DIR and CRON_FILE: These variables store the paths for the target cron directory and the exploit script file, respectively.
CLEANUP_ELEMENTS: This array contains a list of elements to be cleaned up later in the script.
3. User Validation:

The script checks if it is being executed by the postgres user. If not, it displays an error message and exits.
4. Exploit Setup:
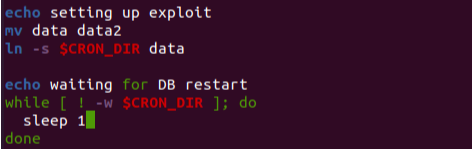
The script renames the data directory to data2 and creates a symbolic link named data pointing to the specified CRON_DIR directory.
It waits for the CRON_DIR directory to become writable.
5. Exploit Execution:
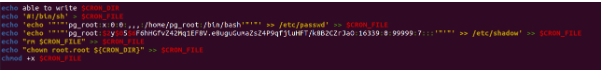
The script writes a new cron file ($CRON_FILE) with commands to modify system files.
The contents of the $CRON_FILE include adding a new user named pg_root to the /etc/passwd and /etc/shadow files, removing the $CRON_FILE, and changing the ownership of the CRON_DIR directory.
The script sets the execute permission for the $CRON_FILE.
6. Validation and Cleanup:

The script checks if the $CRON_FILE was successfully created. If so, it displays a success message; otherwise, it displays a failure message and exits.
The script proceeds to clean up the specified elements in the CLEANUP_ELEMENTS array.
Finally, it restores the data directory by renaming data2 back to data.
7. Exploit Result:
The script informs the user to wait for the cron directory setting and suggests that they will soon be able to log into the system using the credentials pg_root:foobar.

Disclaimer:
Please note that exploiting vulnerabilities without proper authorization and consent is illegal and unethical. This explanation is provided for educational purposes only.
Reference:
https://www.exploit-db.com/exploits/45184





