
A vulnerability in Microsoft Teams could allow attackers to deliver malware to organizations using Teams in its default configuration. The vulnerability, which was discovered by security researchers at JUMPSEC, allows external tenants to bypass client-side security controls that prevent them from sending files to staff in an organization.
The vulnerability works by exploiting a flaw in the way that Microsoft Teams handles internal and external recipient IDs. By manipulating these IDs, attackers can trick Teams into treating them as an internal user, even though they are actually an external tenant. This allows them to send files to users in the organization, even though they are not supposed to be able to do so.
The vulnerability could be exploited to deliver a variety of malware, including ransomware, trojans, and other malicious software. Once the malware is installed on a user's computer, it could be used to steal data, disrupt operations, or even take the computer hostage.Attack Details:
Microsoft Teams allows users with a Microsoft account to communicate with external organizations, which have their own Microsoft tenancies. Messages can be sent between users in different tenancies, with an "External" banner appearing alongside the sender's name.

However, some staff members still click on messages from external tenants, even with the warning, especially if the sender impersonates someone from their own organization using a brand-impersonation domain.
While users can send messages to users in other organizations, there is a limitation when it comes to file sharing. Unlike within their own tenancy, users are blocked from sending files to users in external tenancies. This file-sharing restriction is implemented on the client side in Microsoft Teams, adding a security control.

Messaging a member of the same organization

Restrictions when messaging someone in a different organization
It was discovered that certain security controls in Microsoft Teams are implemented on the client side. Leveraging a traditional Insecure Direct Object Reference (IDOR) technique, The researchers were able to manipulate the recipient ID in the POST request to bypass the security control.
/v1/users/ME/conversations/<RECIPIENT_ID>/messages
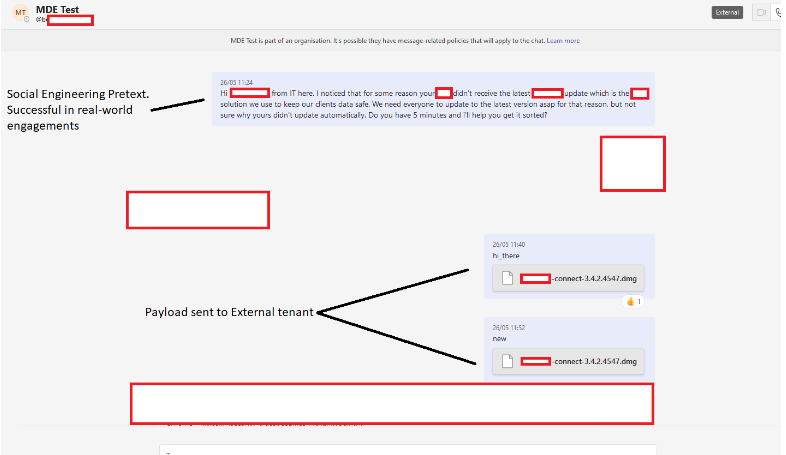
By exploiting this vulnerability, it was found that the payload could be hosted on a SharePoint domain. When the target user downloads the file, it appears directly in their inbox as a file attachment rather than a link. This approach proved successful and provided a more user-friendly and streamlined method for delivering our red team C2 (malware) payload, surpassing traditional phishing techniques.
What’s Next
Microsoft has been notified of the vulnerability, but it has not yet released a patch. In the meantime, organizations that use Teams should take steps to mitigate the risk posed by this vulnerability. These steps include:
Disabling external access to Teams. This will prevent external tenants from sending files to users in the organization.
Educating users about the vulnerability. Users should be made aware of the vulnerability and how to spot and avoid malicious emails and attachments.
Using a security solution that can detect and block malicious files. A security solution can help to protect organizations from malware that is delivered through Teams.
In addition to the above steps, organizations should also consider the following:
Reviewing their Teams permissions settings. Organizations should ensure that only authorized users have the ability to send files to other users in the organization.
Keeping Teams up to date. Microsoft regularly releases security updates for Teams. Organizations should ensure that they are installing these updates as soon as they are available.
Monitoring Teams for suspicious activity. Organizations should use a security solution to monitor Teams for suspicious activity, such as users receiving malicious files or clicking on malicious links.
Call to action:
Organizations that use Microsoft Teams should review the JUMPSEC advisory and take steps to mitigate the risk posed by this vulnerability. By following the steps outlined in this article, organizations can help to protect themselves from malware attacks that are delivered through Teams.
Additional information:
The vulnerability was discovered by security researchers at JUMPSEC.
The vulnerability affects the latest version of Microsoft Teams.
Microsoft has been notified of the vulnerability, but it has not yet released a patch.
Organizations that use Teams should take steps to mitigate the risk posed by this vulnerability.
These steps include disabling external access to Teams, educating users about the vulnerability, and using a security solution that can detect and block malicious files.
Organizations should also review their Teams permissions settings, keep Teams up to date, and monitor Teams for suspicious activity.
The vulnerability is a serious security risk, and organizations should take steps to mitigate the risk as soon as possible.
Conclusion:
The vulnerability in Microsoft Teams is a serious security risk. Organizations that use Teams should take steps to mitigate the risk posed by this vulnerability. By following the steps outlined above, organizations can help to protect themselves from malware attacks that are delivered through Teams.
References:
https://labs.jumpsec.com/advisory-idor-in-microsoft-teams-allows-for-external-tenants-to-introduce-malware/





