
Introduction
CVE-2024-1561 is a critical vulnerability identified in Gradio, a popular Python library for building user interfaces for machine learning models. This vulnerability allows an attacker to gain unauthorized local file read access on the system running the Gradio application. This blog post provides a deep dive into the technical details of CVE-2024-1561, including its exploitation mechanism and potential consequences.
Vulnerability Details
The vulnerability resides in the /component_server endpoint within Gradio applications. This endpoint suffers from a lack of proper authorization checks, allowing attackers to call any method on the Component class with arbitrary arguments. A malicious actor can exploit this by targeting the move_resource_to_block_cache method of the underlying Block class.
Exploitation Flow:
Attacker sends a crafted request to the /component_server endpoint.
The request triggers the invocation of move_resource_to_block_cache method on the Block class.
The attacker controls the arguments passed to this method, including the source and destination paths.
By manipulating these arguments, the attacker can achieve a path traversal attack.
The attacker can specify a source path pointing to any file on the system.
The vulnerable code copies the targeted file to a temporary directory within the block cache.
The attacker can then retrieve the copied file through subsequent requests.
Proof of Concept
To build a PoC lab, we will use following docker configuration which is using a vulnerable version of Gradio, 4.12.0.FROM python:3.8-slim
WORKDIR /usr/src/app
COPY . .
RUN pip install --no-cache-dir gradio==4.12.0
EXPOSE 7860
ENV GRADIO_SERVER_NAME="0.0.0.0"
CMD ["python", "app.py"]The gradio app.py file could simply be:
import gradio as gr
def greet(name):
return f"Hello {name}!"
iface = gr.Interface(fn=greet, inputs="text", outputs="text").launch()Let's build the docker image:
docker build -t gradio-app .
Once the image is ready, let's run it on port 7860:
docker run -p 7860:7860 gradio-app
Now our vulnerable Gradio instance should be accessible at http://localhost:7860/
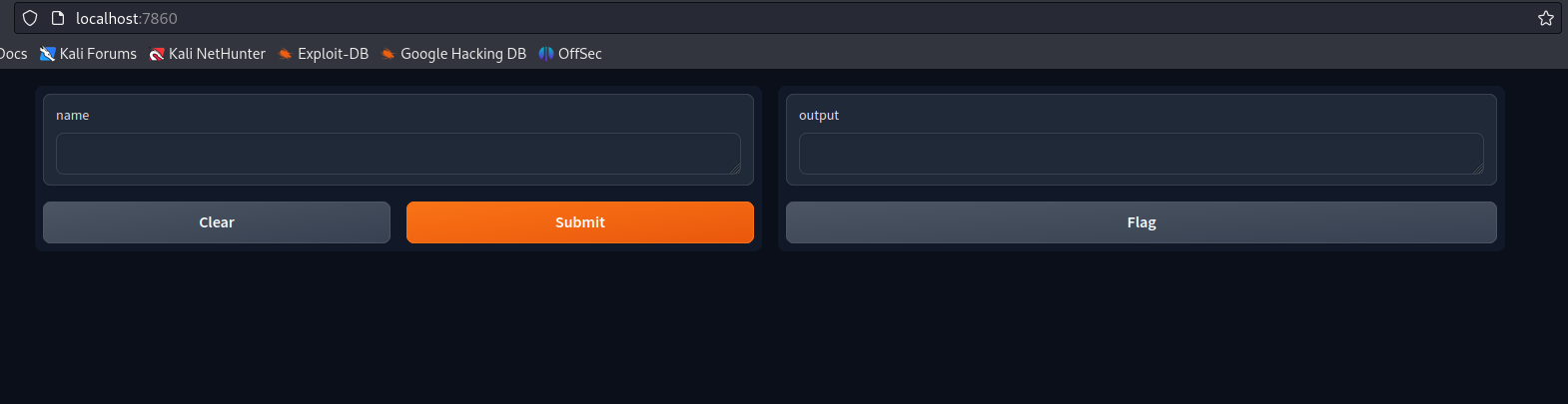
For the exploit, we will be using the following exploit file. But before trying to use it, we will first have to make it executable.
chmod +x CVE-2024-1561To perform the attack, we will use the following command to execute the series of exploits to read a local system file by exploiting CVE-2024-1561:
./CVE-2024-1561 -u http://127.0.0.1:7860 -f /etc/passwd
Impact
This vulnerability poses a significant risk to systems running Gradio applications, especially those exposed publicly through launch(share=True). A successful exploit can grant remote attackers the ability to read arbitrary files on the vulnerable system. This could lead to the following consequences:
Exposure of Sensitive Information: Attackers can access files containing sensitive data such as API keys, configuration files, or even source code.
Lateral Movement: By reading system configuration files, attackers might gather information to facilitate further attacks within the network.
Website Defacement: If the attacker gains access to web server files, they could potentially deface the website.
Remediation
The developers of Gradio have addressed this vulnerability in version 4.13.0 in the following PR#6884. Upgrading to this version or later is crucial to mitigate the risk associated with CVE-2024-1561.
For applications that cannot be immediately upgraded, consider the following workarounds:
Restrict Public Exposure: Avoid exposing Gradio applications directly to the internet. Implement access control mechanisms to limit access only to authorized users.
Minimize File Permissions: Restrict the permissions of sensitive files to prevent unauthorized access even if exploited.
Detection and Prevention
Web Application Security Scanners: Utilize web application security scanners to identify vulnerable Gradio applications within your infrastructure.
Input Validation: Implement robust input validation techniques on the server-side to prevent attackers from crafting malicious requests.
Code Reviews: Regularly conduct code reviews to identify potential security vulnerabilities before deployment.
Conclusion
CVE-2024-1561 highlights the importance of maintaining software libraries and frameworks up-to-date. By understanding the technical aspects of this vulnerability, security researchers can effectively assess its impact, implement appropriate mitigation strategies, and develop robust defenses against similar attacks in the future.
Disclaimer
The information presented in this blog post is for educational purposes only. It is intended to raise awareness about the CVE-2024-1561 vulnerability and help mitigate the risks. It is not intended to be used for malicious purposes.
It's crucial to understand that messing around with vulnerabilities in live systems without permission is not just against the law, but it also comes with serious risks. This blog post does not support or encourage any activities that could help with such unauthorized actions.





