
Introduction
A denial of service vulnerability has been discovered in Django 3.2 before 3.2.20, 4 before 4.1.10, and 4.2 before 4.2.3. The vulnerability is tracked as CVE-2023-36053.
Impact
This vulnerability could allow an attacker to cause a denial of service by sending a specially crafted request to a Django application. The request would cause the application to consume a large amount of CPU time, effectively preventing it from serving other requests.
Technical Details
The vulnerability is a regular expression denial of service (ReDoS) vulnerability in the EmailValidator and URLValidator classes in Django. An attacker can trigger the ReDoS by sending a request with a very large number of domain name labels in the email address or URL. This would cause the regular expression to match an extremely large number of patterns, effectively consuming all of the CPU time on the server.
Here is an example of vulnerable code using EmailValidator:
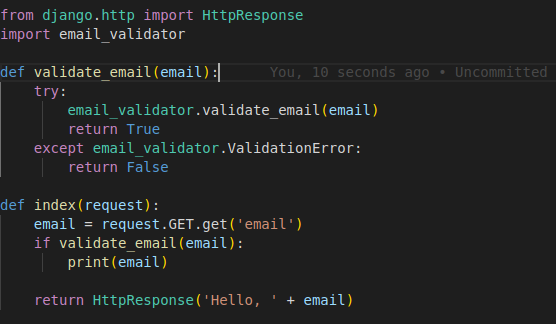
This code is vulnerable to a regular expression denial of service (ReDoS) attack. The email_validator.validate_email() method uses a regular expression to match valid email addresses. If an attacker can control the value of the email parameter, they can craft an email address that contains a very large number of domain name labels. This would cause the regular expression to match an extremely large number of patterns, effectively consuming all of the CPU time on the server.
To mitigate this vulnerability, the code should be updated to use a different regular expression that is not vulnerable to ReDoS. For example, the following regular expression can be used to match valid email addresses:
^[a-zA-Z0-9.+_-]+@[a-zA-Z0-9.-]+\.[a-zA-Z]{2,}$
This regular expression is not vulnerable to ReDoS because it does not contain any loops.
Here is the updated code:

This code is now not vulnerable to ReDoS. By using a different regular expression that is not vulnerable to ReDoS, we can help to protect our application from attack.
Mitigation
The vulnerability has been patched in Django 3.2.20, 4.1.10, and 4.2.3. Users should upgrade to the latest version of Django as soon as possible.
Recommendations
In addition to upgrading to the latest version of Django, users should also consider the following recommendations:
Use a web application firewall (WAF) to protect your Django application from malicious requests.
Keep your Django application up to date with the latest security patches.
Monitor your Django application for suspicious activity.
Conclusion
CVE-2023-36053 is a denial of service vulnerability that could allow an attacker to cause a denial of service by sending a specially crafted request to a Django application. Users should upgrade to the latest version of Django as soon as possible, and implement the other recommendations listed above.





