
Affected Versions
The vulnerability affects PaperCut MF/NG versions 8.0 and above, but prior to versions 20.1.7, 21.2.11, or 22.0.9.
Impact
An attacker with access to the vulnerable web interface could exploit this vulnerability to gain SYSTEM privileges on the target system. This could allow them to take control of the system and execute arbitrary commands.
Mitigation
The vulnerability has been fixed in PaperCut MF/NG versions 20.1.7, 21.2.11, and 22.0.9. Users should update to the latest version of PaperCut MF/NG to mitigate this vulnerability.
Remediation
If you are unable to update to the latest version of PaperCut MF/NG, you can mitigate the vulnerability by disabling the SetupCompleted class. To do this, you can edit the papercut.properties file and add the following line:
setupcompleted.class=disabled
Once you have added this line, you can save the papercut.properties file and restart the PaperCut MF/NG service.
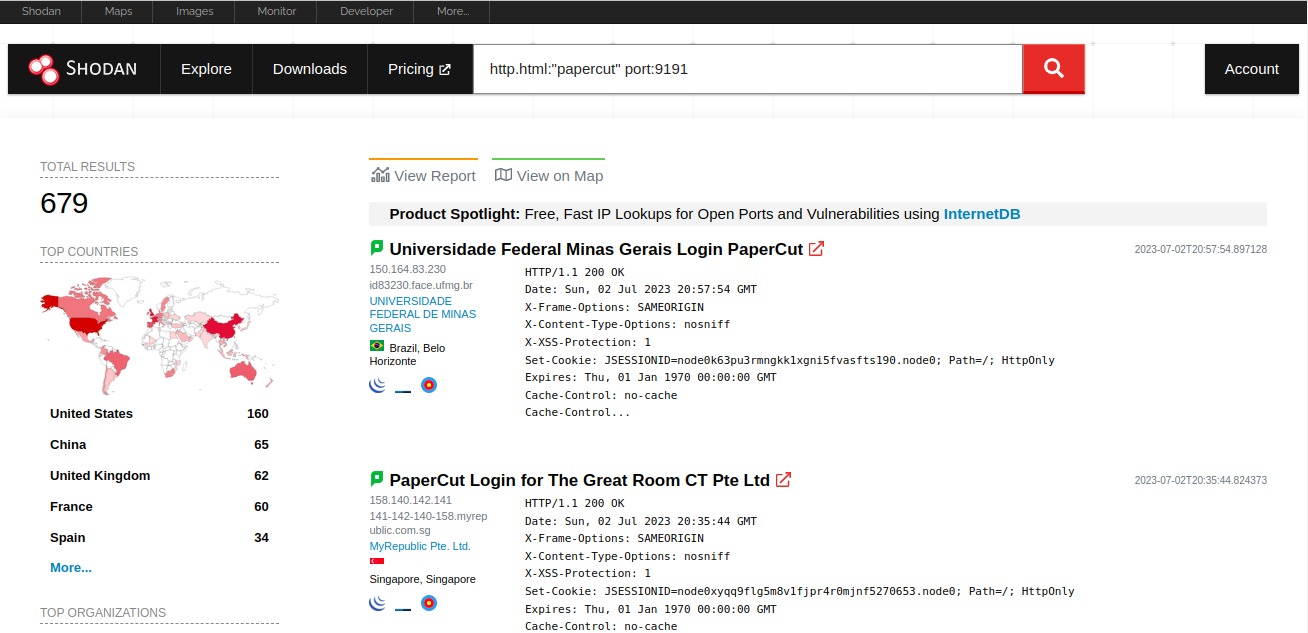
Shodan Dorks:
http.html:"papercut"
http.html:"papercut" port:9191
http.title:"PaperCut Login"
Technical Details
The vulnerability in CVE-2023-27350 exists in the SetupCompleted class. This class is responsible for processing the results of the setup wizard. When the setup wizard is completed, the SetupCompleted class is called. The SetupCompleted class checks to see if the user has entered a valid license key. If the user has entered a valid license key, the SetupCompleted class proceeds to install PaperCut MF/NG. If the user has not entered a valid license key, the SetupCompleted class displays an error message.
The issue with the SetupCompleted class is that it does not properly validate the "service" parameter in URL requests. This allows attackers to pass arbitrary values to the "service" parameter, which can then be used to access protected pages or execute arbitrary code.
For example, an attacker could pass the following value to the "service" parameter:
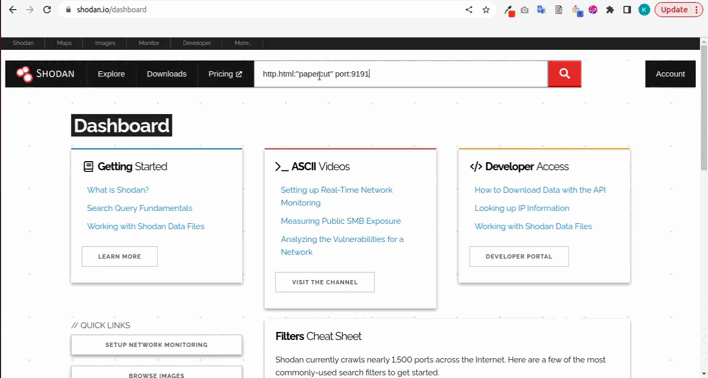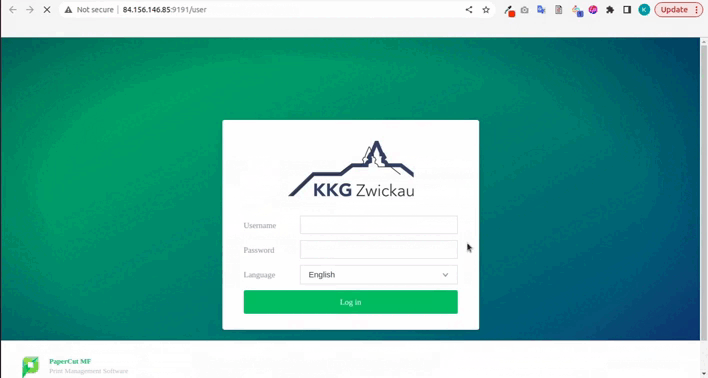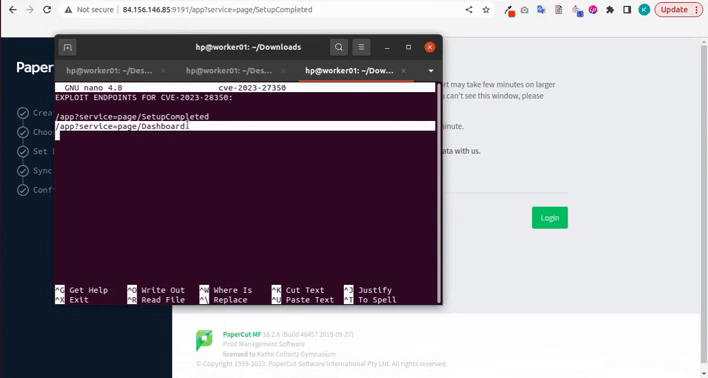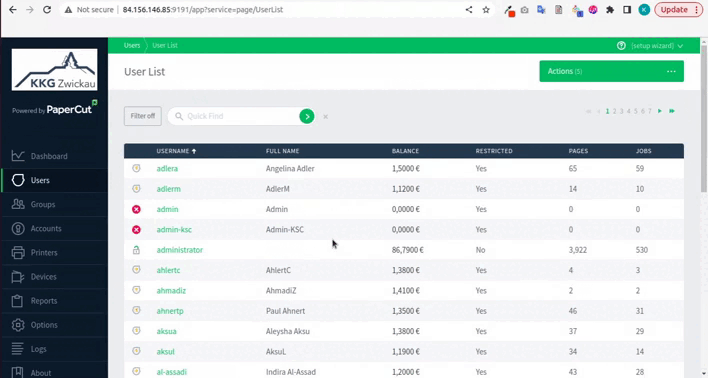
/app?service=page/SetupCompleted?command=ls
This would cause the SetupCompleted class to execute the ls command on the PaperCut server. This would allow the attacker to list the contents of the current directory on the server.
Similarly, an attacker could also pass the following value to the "service" parameter:
/app?service=page/Dashboard
This would cause the SetupCompleted class to redirect the attacker to the Dashboard page, which is accessible to users who have logged in to the PaperCut application. If the attacker is not logged in, they would be able to bypass authentication and access the Dashboard page.
Summary
CVE-2023-27350 is an authentication bypass vulnerability in PaperCut MF/NG print management software. The vulnerability exists in the SetupCompleted class, which is responsible for processing the results of the setup wizard. The vulnerability can be exploited by an attacker to bypass authentication and execute arbitrary code as SYSTEM on vulnerable targets. Users should update to the latest version of PaperCut MF/NG to mitigate this vulnerability. If you are unable to update to the latest version of PaperCut MF/NG, you can mitigate the vulnerability by disabling the SetupCompleted class.





