
Introduction:
The open-source workflow management platform, Apache DolphinScheduler, faced a critical vulnerability: CVE-2022-45875. This vulnerability, categorized as Improper Input Validation, potentially exposed systems to Remote Code Execution (RCE) attacks, granting attackers complete control over affected systems. In this blog, we'll delve deep into the technical details of CVE-2022-45875, understanding its root cause, exploitation methods, mitigation strategies, and best practices to secure your DolphinScheduler deployments.
Vulnerability Breakdown:
The heart of the vulnerability lies in DolphinScheduler's alert system. Alerts in DolphinScheduler allow users to define triggers based on specific conditions, notifying them upon occurrence. These alerts can be configured to execute scripts to perform actions like sending emails or running system commands. The vulnerable functionality resides in the script type alert, where user-provided input is insufficiently validated before being embedded and executed within a shell script.
Exploitation Paths:
Attackers can exploit CVE-2022-45875 by injecting malicious code into various user-controlled inputs within the script type alert configuration. Some potential injection points include:
Alert name: Injecting commands into the alert name can trigger them unintentionally.
Script content: Directly injecting commands within the script content allows direct execution upon triggering the alert.
Alert variables: Exploiting variable expansion mechanisms within the script can lead to code execution.
Alert condition: Embedding commands within the alert condition can trigger script execution on fulfilling the condition.
Exploit Proof of Concept:
Install and setup DolphinScheduler:
docker run --name dolphinscheduler-standalone-server -p 12345:12345 -p 25333:25333 -d apache/dolphinscheduler-standalone-server:"3.0.0"Login to dashboard: http://localhost:12345/dolphinscheduler/ui Default credentials are ‘admin’:’dolphinscheduler123’

Create an alarm script: Get docker container ID:
docker ps -aGet into container’s shell:
sudo docker exec -it <container_id> bash
Go to tmp directory:
cd /tmp/Create an alarm script with 777 permissions to create new file in same directory on running:
echo "touch /tmp/alarm1triggered" > alarm1.sh
chmod 777 alarm1.sh

Create a tenant in DophinScheduler: Go to Security/Tenant Manage and click on Create Tenant
Assign that tenant to admin user: Go to Security/User Manage and click on the edit button on admin user. Assign the tenant you just created to this user and save it.
Create an alarm: Go to Security/Alarm Instance Manage and click on Create Alarm. Select “script” as plugin. Write following details and save it: User Params:
'; echo "This has successfully performed shell injection attack" > /tmp/attack.txt; #Script Path:
/tmp/alarm1.sh
Create a project and workflow: Go to Project and click on Create Project. Go to the Workflow Definition tab under the details of the project you just created and click on Create Workflow. Drag and drop the Shell option under the workflow definition window. Write a name and whatever script you would like it to run in its details and save it (select the correct tenant while saving it).
Run the workflow: Click on the Online icon on the workflow you just created. Once its status becomes online, we can click on the Start icon to run it. This should trigger the alarm script we have associated with our tenant.

Verify the attack execution: Go to the docker container’s /tmp/ directory and verify the creation of the alarm1triggered.sh file. If that file creation ran the shell commands we had injected then it should also have created the attack.txt file with text “This has successfully performed shell injection attack”.

Impact and Consequences:
Successful exploitation of CVE-2022-45875 grants attackers a foothold within the system, enabling them to:
Execute arbitrary commands on the system: This allows attackers to steal data, modify files, deploy malware, or disrupt critical operations.
Gain elevated privileges: By exploiting additional vulnerabilities or escalating privileges, attackers can gain complete control over the system.
Launch lateral attacks: Compromise other systems connected to the vulnerable deployment.
Mitigation and Patching:
Fortunately, Apache released patches addressing CVE-2022-45875 for various DolphinScheduler versions:
3.0.2 and later: Upgrade to versions 3.0.2 or 3.1.1.
They have added if conditions to identify attempts to inject shell scripts in the patch commit:
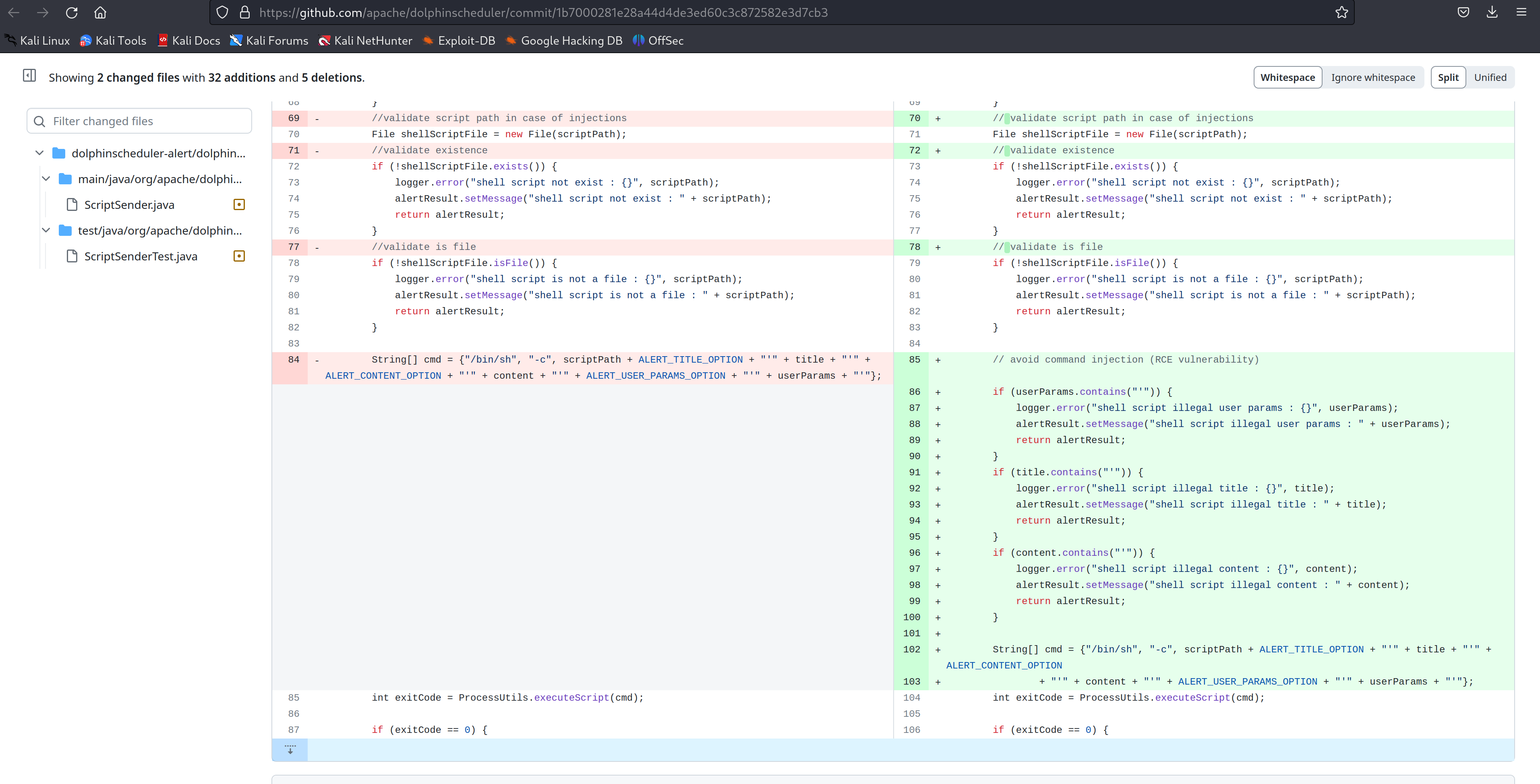
Additionally, implementing the following security best practices can further strengthen your DolphinScheduler deployment:
Minimize user privileges: Grant users only the minimum permissions necessary for their tasks.
Enable authentication and authorization: Implement robust authentication and authorization mechanisms to restrict access to sensitive resources.
Regularly update dependencies: Keep DolphinScheduler and other dependencies up-to-date with the latest security patches.
Monitor and review logs: Monitor system logs for suspicious activity and regularly review alert configurations for potential injection vectors.
Conduct security assessments: Perform regular security assessments to identify and address vulnerabilities in your DolphinScheduler deployment. White Hack Labs identifies new vulnerabilities introduced by incremental code movement and is designed to provide you with constant, comprehensive, and efficient security testing coverage.
Conclusion:
CVE-2022-45875 serves as a stark reminder of the importance of proper input validation, particularly in security-sensitive systems. By patching vulnerable versions, implementing best practices, and maintaining a security-focused approach, organizations can effectively mitigate the risks associated with this vulnerability and safeguard their DolphinScheduler deployments.
Further Resources:
Apache DolphinScheduler Security Bulletin: https://www.apache.org/security/
Disclaimer
The information presented in this blog post is for educational purposes only. It is intended to raise awareness about the CVE-2022-30190 vulnerability and help mitigate the risks. It is not intended to be used for malicious purposes.
Exploiting vulnerabilities in live systems without proper authorization is illegal and harmful. This blog post does not advocate or encourage such activities.





