
On June 16, 2023, Progress Software disclosed a third vulnerability impacting its MOVEit Transfer application. This vulnerability, which is being tracked as CVE-2023-35708, is an SQL injection vulnerability that could allow an unauthenticated attacker to gain unauthorized access to the MOVEit Transfer database.
The vulnerability exists in the MOVEit Transfer web application. When an attacker submits a specially crafted request to the application, they can inject arbitrary SQL commands into the database. This could allow the attacker to view, modify, or delete data in the database, or even execute arbitrary commands on the underlying operating system.
This vulnerability is particularly concerning because it is the third vulnerability to be found in the MOVEit Transfer app in recent months. In March 2023, two other vulnerabilities were disclosed, both of which could be exploited by attackers to gain unauthorized access to the application.
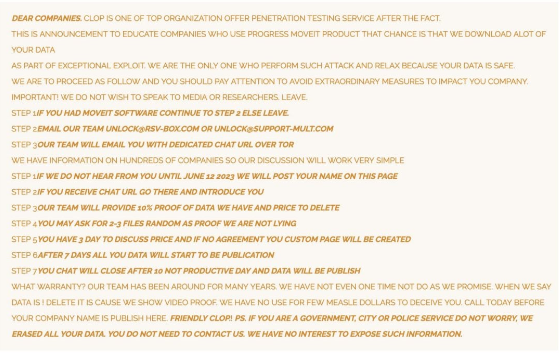
The Cl0p ransomware gang has been exploiting these vulnerabilities to target organizations around the world. In recent weeks, the gang has claimed to have infected over 27 organizations, including several U.S. federal agencies.
Progress Software has released a patch to address this vulnerability. Organizations that are using MOVEit Transfer should apply the patch as soon as possible to protect themselves from attack.

Technical Details of the Vulnerability
The CVE-2023-35708 vulnerability exists in the MOVEit Transfer web application. When an attacker submits a specially crafted request to the application, they can inject arbitrary SQL commands into the database. This is done by exploiting a flaw in the way that the application handles user input.
The vulnerability can be exploited by submitting a request to the application that contains a malicious SQL command. The application will then execute this command, which could allow the attacker to view, modify, or delete data in the database, or even execute arbitrary commands on the underlying operating system.
Mitigation Strategies
There are a number of mitigation strategies that organizations can implement to protect themselves from this vulnerability. These include:
Applying the patch that has been released by Progress Software.
Using a web application firewall (WAF) to filter out malicious requests.
Implementing input validation to prevent malicious SQL commands from being injected into the database.
Monitoring the application for suspicious activity.
Conclusion
The CVE-2023-35708 vulnerability is a serious security issue that could be exploited by attackers to gain unauthorized access to the MOVEit Transfer application. Organizations that are using MOVEit Transfer should apply the patch that has been released by Progress Software as soon as possible to protect themselves from attack.
In addition to applying the patch, organizations should also implement other mitigation strategies to protect themselves from this vulnerability. These include using a WAF, implementing input validation, and monitoring the application for suspicious activity.





