
GNU Screen is a terminal multiplexer that allows users to run multiple independent sessions in a single terminal window. It is a popular tool for system administrators and developers.
CVE-2023-24626 is a vulnerability in GNU Screen that allows local users to escalate their privileges. The vulnerability exists in the way that GNU Screen handles signal sending. When a signal is sent to a process, GNU Screen does not properly check the permissions of the sender. This can allow a local user to send a privileged signal to any process, including processes that are running with root privileges.
The vulnerability affects GNU Screen versions prior to 4.9.0. The vulnerability has been patched in version 4.9.0, so users are advised to upgrade to the latest version as soon as possible.
Impact of the vulnerability
The impact of CVE-2023-24626 is that a local user can escalate their privileges to root. This could allow the attacker to take control of the system, steal data, or install malware.
Technical details
The vulnerability in GNU Screen is caused by a flaw in the way that the socket.c file handles signal sending. When a signal is sent to a process, the socket.c file does not properly check the permissions of the sender. This can allow a local user to send a privileged signal to any process, including processes that are running with root privileges.
The vulnerability can be exploited by a local user to escalate their privileges by sending a privileged signal to a process that is running with root privileges. The signal that is sent will depend on the privileges that the attacker wants to escalate to. For example, to escalate to root privileges, the attacker would send the SIGKILL signal to a process that is running with root privileges.
Exploit Code Explanation
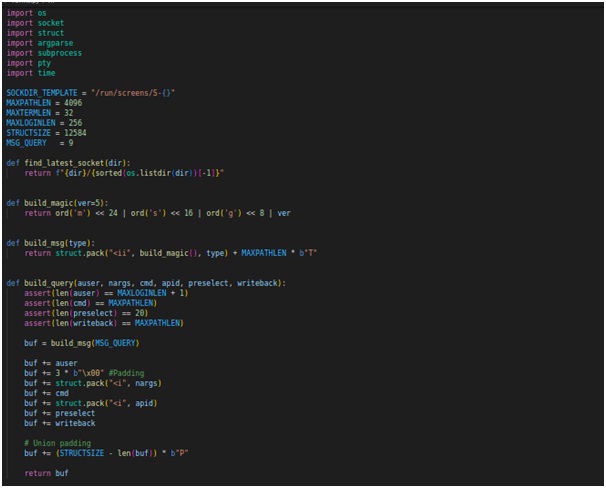
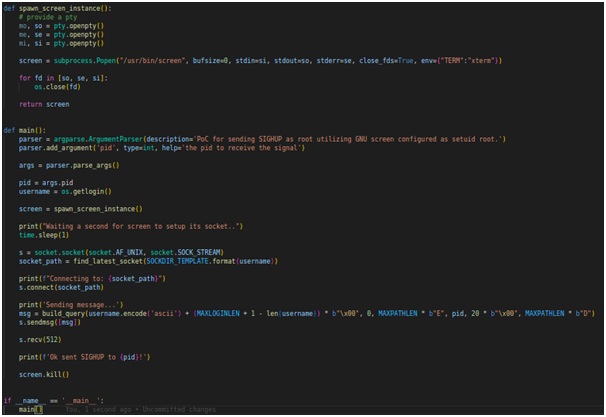
This Python script is a Proof of Concept (PoC) for a Privilege Escalation vulnerability in GNU Screen version 4.9.0. The PoC demonstrates how an attacker can escalate privileges and send the SIGHUP signal to a specified process, effectively enabling the attacker to execute arbitrary commands as a privileged user.
Let's break down the key components of the PoC script:
Constants and Functions: The script sets up constants such as SOCKDIR_TEMPLATE, MAXPATHLEN, MAXTERMLEN, MAXLOGINLEN, and STRUCTSIZE for use in the exploit. It also defines helper functions like find_latest_socket and build_magic.
Building the Message: The build_msg function constructs a message with a specific type for communication with the vulnerable GNU Screen instance.
Sending the Exploit: The main function is the core of the PoC. It parses command-line arguments to receive the target process ID (pid). It then spawns an instance of GNU Screen using the spawn_screen_instance function and connects to the latest socket created by GNU Screen.
Exploiting the Vulnerability: The script prepares the payload by constructing a query message using the build_query function. The crafted message includes data such as the user, command, preselect, and writeback. By sending this message to the vulnerable GNU Screen, the script leverages the vulnerability to escalate privileges and send the SIGHUP signal to the specified process (pid).
Cleaning Up: The script ensures proper cleanup by terminating the spawned instance of GNU Screen using screen.kill().
Mitigation
The vulnerability can be mitigated by upgrading to GNU Screen version 4.9.0 or later. Users who cannot upgrade should disable the setuid and setgid flags on the GNU Screen binary.
To disable the setuid and setgid flags on the GNU Screen binary, you can use the following command: sudo chmod -s screen
This will prevent the GNU Screen binary from being run with elevated privileges.
Additional information
CVE-2023-24626 on the NVD: https://nvd.nist.gov/vuln/detail/CVE-2023-24626
CVE-2023-24626 on Debian Security Tracker: https://security-tracker.debian.org/tracker/CVE-2023-24626
CVE-2023-24626 on Red Hat Customer Portal: https://access.redhat.com/security/cve/cve-2023-24626
I hope this blog post has been informative. If you have any other questions, please feel free to ask.





